The Reason that Face Recognition is Chosen for Access Control Management
Face recognition is secure because it is difficult to spoof, and it can be lost or stolen. Reduces security risks and eliminates the need for reissuance It is also effective for improving operational efficiency. Smooth access and management It can be realized, and convenience is highly appreciated by both users and administrators.

Breadcrumb navigation
 The reason we recommend Face Recognition for Access Control Management
The reason we recommend Face Recognition for Access Control Management
NEC Solution Innovators recommend face recognition for strict access control management on facilities including offices.
Face recognition authenticates by matching the image of the person stored in the database with the face image of the target person taken with a camera. It is secure because it is difficult to spoof, and there is no need to have a physical key or IC card, or set a password. It is also effective in improving operational efficiency by reducing security risks due to loss or theft and eliminating the hassle of reissuance. In addition, since it is non-contact and does not require operations such as holding a finger, it can also be used as a countermeasure against infectious diseases in access control.
Various issues when installing access control management system
![]() Considering replacing existing access control systems...
Considering replacing existing access control systems...
 I feel that the security of my existing system is a challenge
I feel that the security of my existing system is a challenge- Risk of forgetting or losing an employee's IC card, and the time and effort required to deal with it
- Risks associated with lending and borrowing IC cards between employees and lending them to outsiders
 It takes a lot of time and effort to measure the temperature of infectious disease control and record it
It takes a lot of time and effort to measure the temperature of infectious disease control and record it
![]() Considering implementing new access control system...
Considering implementing new access control system...
 Wishing to introduce an access control system that is highly convenient for managers
Wishing to introduce an access control system that is highly convenient for managers Wishing to introduce an access control system that is highly convenient for employees (users)
Wishing to introduce an access control system that is highly convenient for employees (users) Wishing to install access control management system with high security
Wishing to install access control management system with high security
Benefits for Face Recognition Access Control Management System Installation
![]() High Security Strength
High Security Strength
- Possible to prevent people who are not eligible to enter the room by lending or borrowing an IC card or accompanying them.
- Prevent security risks of loss of IC cards.
- Authentication by the camera and the fact that the information at the time of verification remains as a "face image log" has a high fraud deterrent effect.
![]() Easy to Record Entry/Exit Record
Easy to Record Entry/Exit Record
- Entry and exit records are kept as a face image log, so administrators can visually check them.
- *With cards, fingerprint authentication, vein authentication, etc., it is difficult for the administrator to determine who is who is at a glance.
![]() Countermeasure Against Infectious Diseases
Countermeasure Against Infectious Diseases
- It is touchless and hygienic. The thermal camera can perform facial recognition while simultaneously measuring and recording the surface temperature of the body.
- If the person being authenticated has a fever, the door will not open.
- By recording entry and exit times as well as the duration of stay, it becomes easier to trace the path in case an infection occurs.

![]() High convenience for administrators
High convenience for administrators
- No need to handle forgotten IC cards.
- Once registered, it can adapt to aging changes and automate the face registration process after the system starts operating(Bio-IDiom's function).
- Basic authentication functions can continue to be used even during malfunctions(Bio-IDiom's function).

![]() High convenience for users
High convenience for users
- No need to carry IC cards, eliminating the risk of loss and the need for procedures when forgotten.
- Entry can be granted by simply showing one’s face (walk-through authentication while carrying luggage).

 Type of Authentication Methods and Positioning of Face Recognition
Type of Authentication Methods and Positioning of Face Recognition

Type of Authentication
Identity verification methods are divided into three methods: "knowledge authentication," "property authentication," and "biometric authentication."
Knowledge Authentication
It is a method of authenticating a person who knows a specific combination of numbers or strings of numbers, such as a password or PIN, as the only person. Since you don't need to carry it, you don't have to worry about losing it, but there is a risk that you will forget it or someone else will guess it.In addition, in recent years, it has become more complicated in terms of convenience, such as the need to combine uppercase and lowercase letters, numbers, and special symbols to 10 characters or more when typing. These passwords are also difficult to remember, so writing them down creates new risks, such as passwords being stolen.
Property Authentication
It is an authentication method in which the only person is a possession such as a general door key, card key, employee ID, membership card, ID card, IC card, etc. The disadvantage of property authentication is that there is a risk of forgetting the possession to prove your identity, or losing it, impersonating it, or stealing it.
Biometric Authentication
"Biometric authentication" overcomes the disadvantages of "knowledge authentication" and "property authentication" and aims to achieve both convenience and safety. You don't need to have a key or employee ID card to verify your identity, and you don't need to remember your password. Since biometric authentication uses the unique physical characteristics of each person as a "key", it is difficult to impersonate or counterfeit, and is suitable for identity verification in situations where reliable security is required.In this way, biometric authentication is a technology that can pursue safety and convenience, and "face recognition" can be said to be superior in both aspects. Compared to biometric authentication such as fingerprint authentication, palm print recognition, vein recognition, voice biometric recognition, and iris recognition, it does not require a special device and can be authenticated with a general-purpose small camera. It is also expected to be used in walk-through types that allow you to verify your identity just by passing through without stopping, and at the entrance gate of facilities that need to handle a large number of people in a short period of time. It also meets the needs for non-contact and non-face-to-face contact as a measure to prevent infection with the new coronavirus.

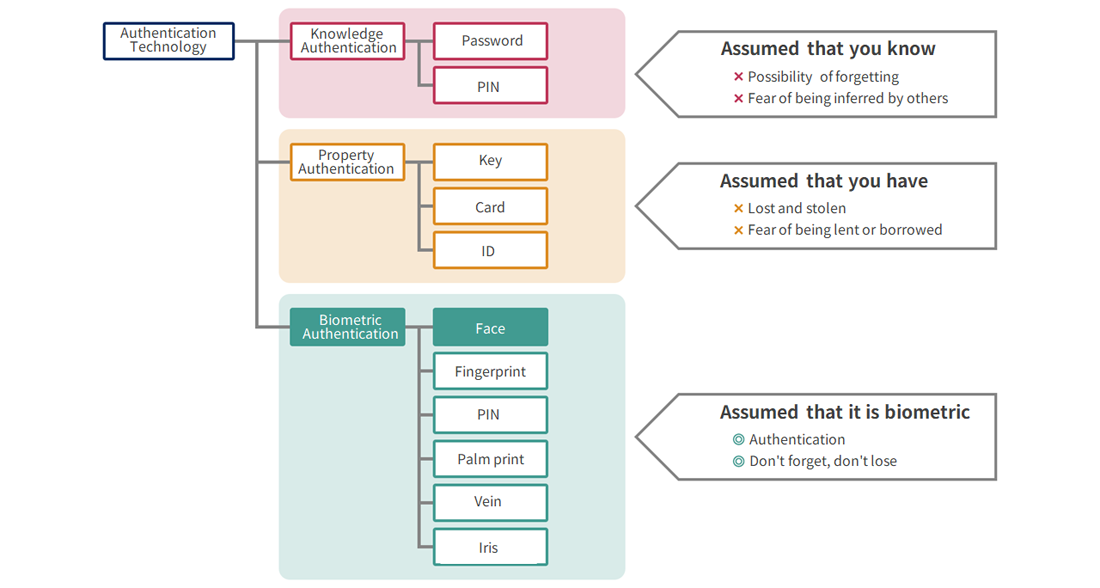
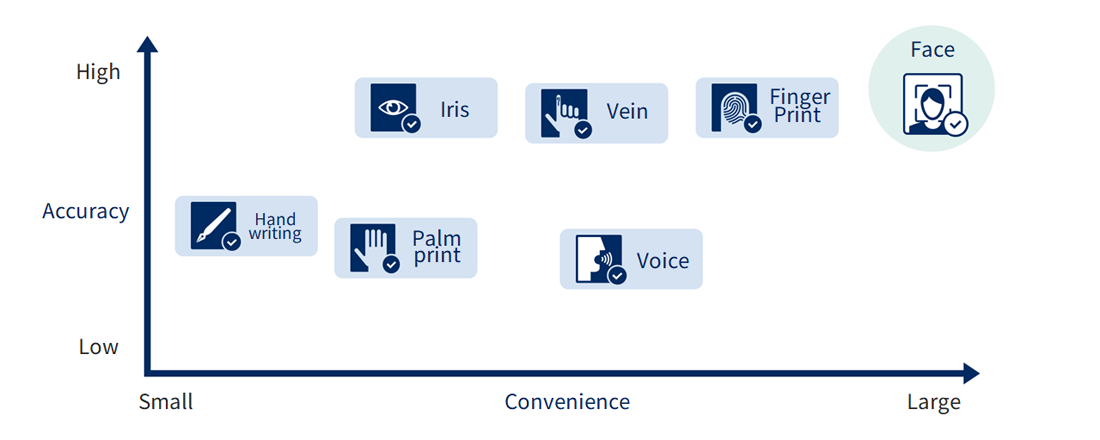
Chart: "Positioning of each technology in biometric authentication", face recognition is a very convenient authentication method. In addition, advances in deep learning have greatly improved the accuracy of face recognition. In this way, it can be said that face recognition is a method that combines both convenience and high authentication accuracy.
 The Reason Bio-IDiom KAOATO is chosen
The Reason Bio-IDiom KAOATO is chosen
Why "Bio-IDiom KAOATO" is chosen?
Functions that match customer needs and high-precision face recognition based on a wealth of experience achieve "ease of use" and "high reliability"
| Feature | Description | Value provided |
| Face recognition technology with boasting high accuracy |
|
|
|---|---|---|
| Abundant implementation experience |
|
|
| System Scalability |
|
|
| Useful functions for operation |
|
|
You can read more about Bio-IDiom KAOATO, the face recognition package software, from the overview to what it can do, and the fields of application of face recognition here. Examples of Bio-IDiom KAOATO in action.
Here are some examples of how facial recognition can be used in offices, manufacturing, real estate development, and the medical industry. Please take a look.
Bio-IDiom KAOATO Value
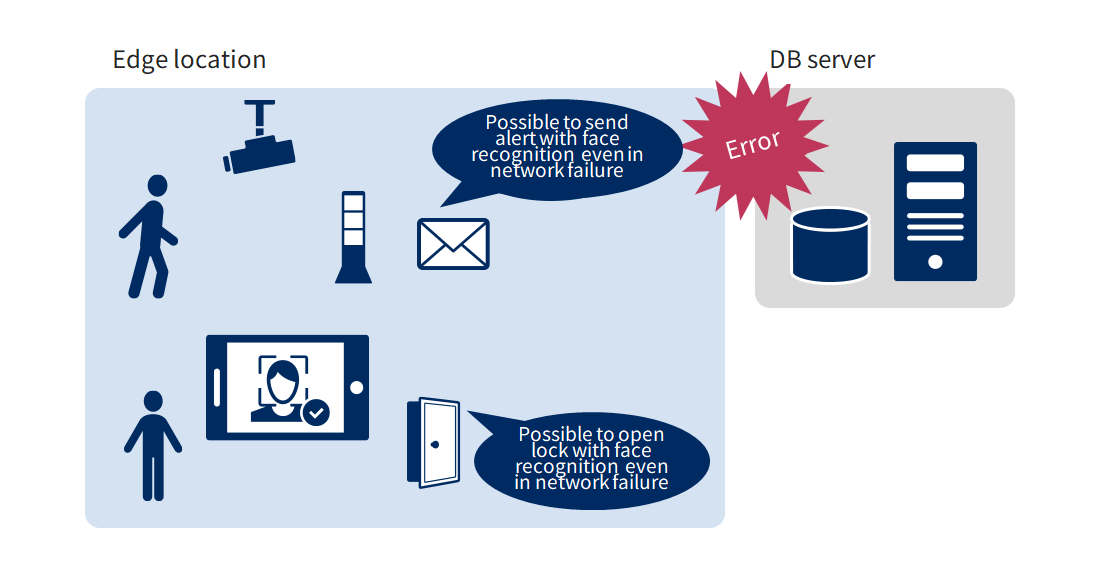
Even in the event of a network failure, basic authentication functions can be used continuously.
Equipped with degraded operation* in the event of a database failure.

|
- *Degraded operation, degraded operation: The practice of restricting the function or performance of a system or switching to another system or system to keep the system usable when the normally used method or system does not function properly.
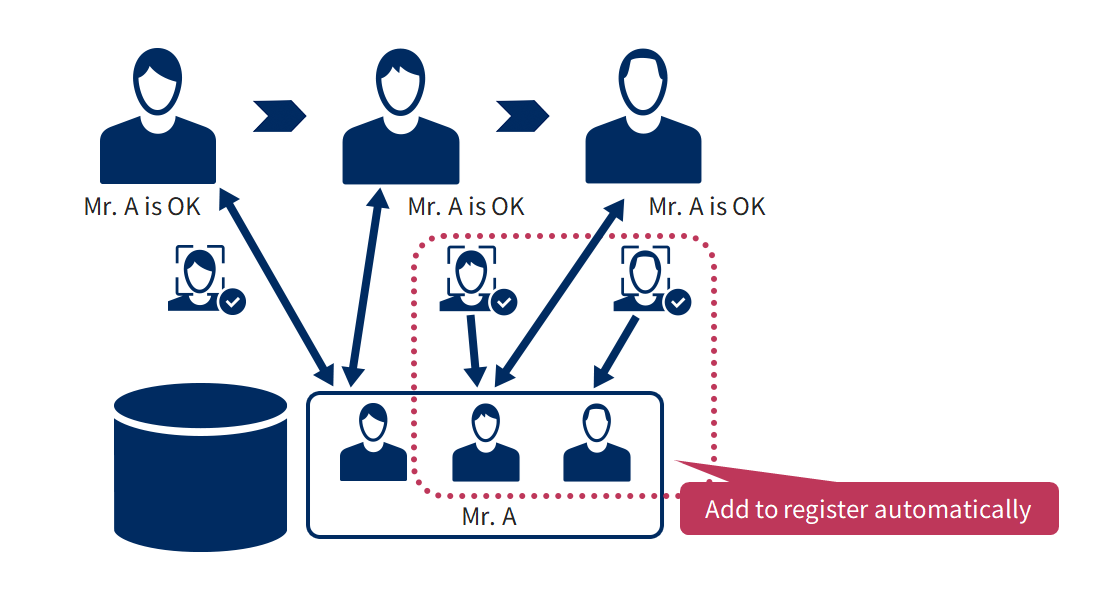
Automate face registration work after the start of operation.
Respond to changes over time by making additional registrations based on score criteria.

|
Adding and condensing knowledge gained from numerous implementation results to KAOATO functions.

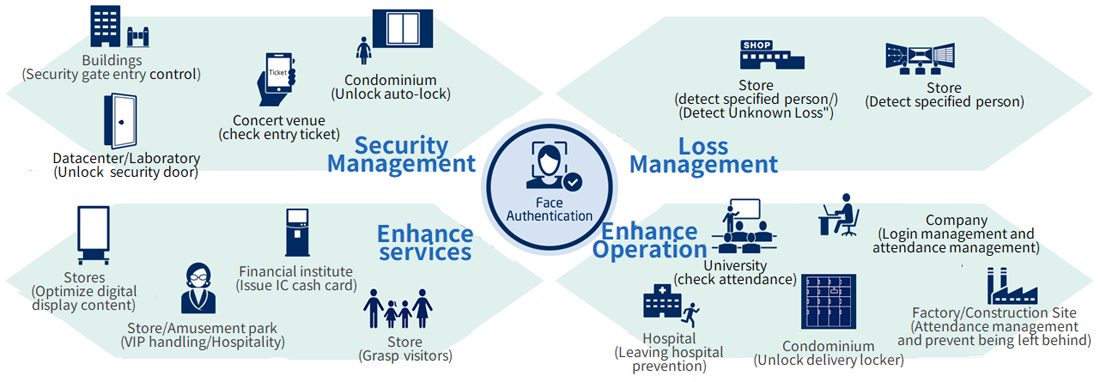
Adding and condensing knowledge gained from numerous implementation results to KAOATO functions.
If you have any questions about access control or face recognition package software Bio-IDiom KAOATO, please feel free to contact us.