Column for Access Control Management and Face Recognition
Why is Face Recognition System attracting attention now?
Benefits and utilization methods are explained!

Breadcrumb navigation
 Table of Contents
Table of Contents
A face recognition system is a system that determines whether a person is who he or she says he or she is based on the information possessed by a person's face. With the increase in security awareness, these systems are being used for building access control, bank identification, and preventing impersonation at concert venues. When actually introduced, these systems can provide many benefits by integrating with a variety of internal systems.
1. Why is Face Recognition System attracting attention now? Explanation of advantages and utilization!
Identification of smartphones (smart phones), office security measures, and prevention of impersonation at live venues... Face recognition systems are now being introduced in many facilities and products as “easy-to-use, high-security authentication systems. However, many people may not know the details of the system and its advantages.
This section provides a detailed explanation of the basics of face recognition systems, including what they are, their features, how they can be used, and what to look for when introducing them. We hope you will find this information useful when considering security measures within your company or facility.
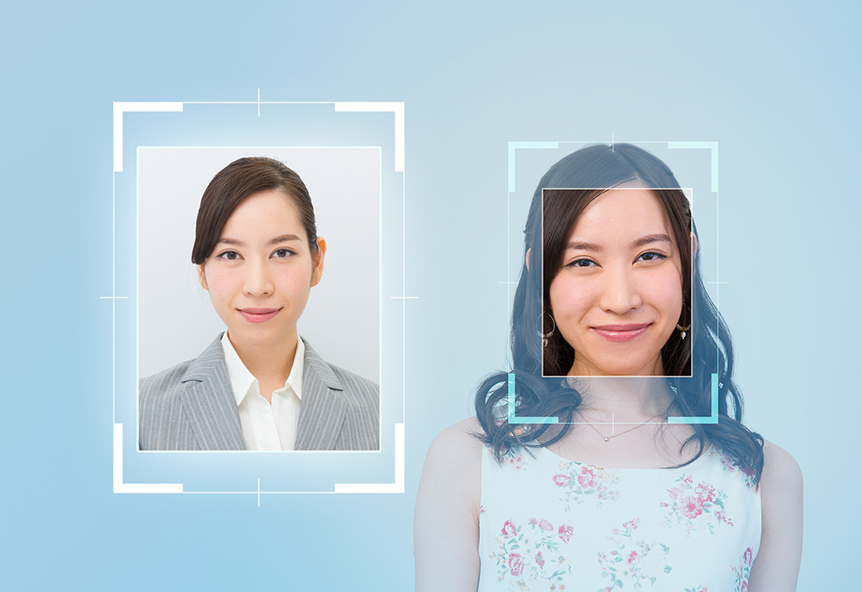
2. What is a face recognition system?
A system that identifies a person based on his/her innate physical characteristics (fingerprints, iris of the eye, voice, etc.) is called a “biometric authentication system (biometric authentication)". Since biometric authentication is the unique information that each person possesses, it is difficult to counterfeit and is said to have a very high level of security. Among these systems, “face recognition systems” are those that identify individuals by their facial features such as eyes, nose, and mouth. Unlike fingerprints, the face is a means by which anyone can identify a person, and unlike fingerprints, a manager can quickly recognize a person who has been authenticated. For this reason, biometric authentication systems are attracting attention as a system that reduces the psychological burden on users.

| For a detailed explanation of the Bio-IDiom KAOATO face recognition packaged software, including an overview, what it can do, and the application fields of face recognition, please refer to this page. About Bio-IDiom KAOATO |
|---|
Click here to contact us for more information about face recognition.
3. How does a face recognition system work?
The detailed mechanisms of face recognition systems vary depending on the company developing the system. In this article, we will provide an easy-to-understand explanation with reference to NEC's face recognition engine, which boasts the world's No. 1* rated accuracy .
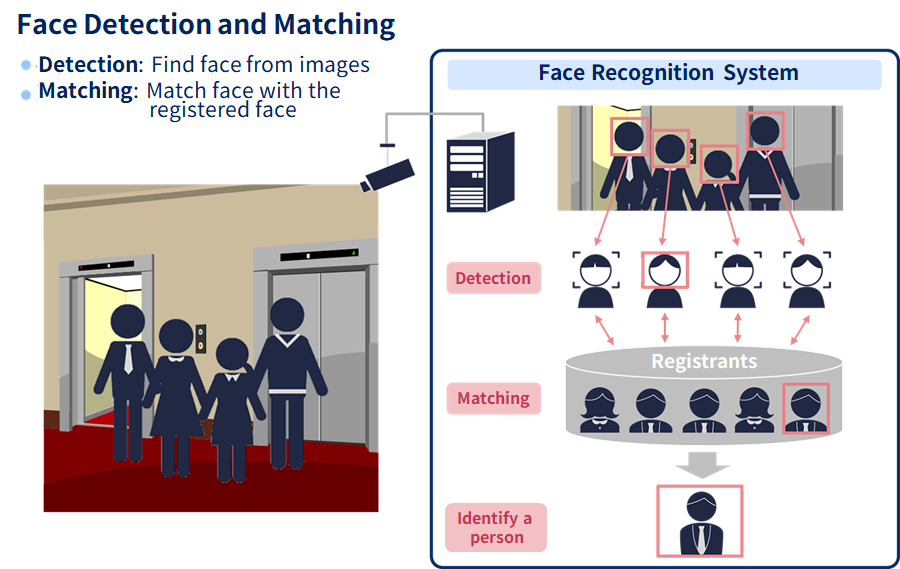
A face recognition system first reads an individual's face from a video or image, and then analyzes the position of feature points (parts that are characteristic) such as the eyes, nose, and mouth, as well as the size of the face area.
The analyzed data is encrypted and stored on a server to prevent external theft. In this way, when a person turns his or her face to the camera for authentication, the actual face is matched with the stored data to confirm the person's identity.
- *
 No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.
4. Why are face recognition systems attracting attention now?
So why are face recognition systems attracting so much attention today? There are two main reasons. One is the increasing importance of security measures in the corporate world, where personal and customer information has been leaked due to theft and misuse of PCs.
Companies are increasingly required to take security measures to protect their valuable assets. Against this backdrop, high-security face recognition systems are now widely used for access control in office buildings and for identification at airports. Another factor is the dizzying evolution of face recognition systems, which in 2001 had a low error rate and was considered questionable for practical use. In the latest evaluation test (FRVT2018) by NIST published in 2018, NEC achieved a dramatic reduction in the authentication error rate and achieved performance that is both highly reliable (authentication accuracy) and convenient (search speed).
Furthermore, more and more facial recognition systems are being introduced in many places, as they are able to handle changes in makeup, hair style, and facial changes over time.The market for facial recognition is growing explosively, and is expected to grow to 5.8 billion yen in 2022, approximately 3.6 times the market size from 2018. (*) It is expected that the market will be introduced in even more places in the future.
* Research on the domestic market for security-related equipment, systems, and services|Fuji Keizai (January 9, 2020)
For inquiries about the 'Bio-IDiom KAOATO' face recognition software package, equipped with the world's No. 1* rated face recognition engine and featuring high recognition accuracy, which can prevent unauthorized office access while enhancing convenience, please contact us here.
- *
 No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.
5. What are the advantages of face recognition systems?
What are the advantages of implementing a face recognition system?
The following is an introduction from five major perspectives.
(1) Ease of use and high level of security
First of all, face recognition systems are characterized by a higher level of security than other authentication systems. Information on a person's face cannot be stolen like a PIN or IC card, and it is extremely difficult to counterfeit. In addition, since the system identifies the face of each individual in access control, it detects and informs the manager if two or more people enter or leave a room at the same time, thereby preventing people from entering or leaving together.In terms of security level, iris and vein authentication are on par with face recognition systems. However, when it comes to ease of use, face recognition systems have a significant advantage over other biometric systems. Fingerprint and vein authentication require the user to place his or her finger on the device for authentication, but with face recognition, all the user has to do is point his or her face at the camera. Users do not feel particularly stressed, and can pass smoothly even when their hands are full.
This combination of convenience and security is the strength of the face recognition system.
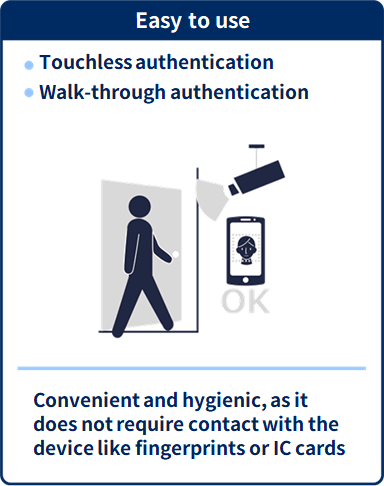
(2) Hygienic due to non-contact
Face recognition systems are very hygienic because there is no need to touch anything.
In the age of the New Normal, we must also contend with the risk of infectious diseases.
Therefore, “non-contact” authentication systems, such as face recognition systems, are very effective in reducing the spread of viruses.
(3) Easy to install, with no need for specialized equipment
Unlike other biometric authentication systems, face recognition systems do not require specialized equipment; all that is needed is a webcam (including IP cameras) and a server for storing data (also available in the cloud). Compared to vein and iris authentication, which require specialized equipment, facial recognition systems are relatively easy to implement.
(4) No risk of losing or forgetting passwords
Many companies use PINs or IC cards for access control. In this case, it is inevitable that employees may forget or lose their passwords or cards. If the card is lost, it could fall into the hands of a malicious third party and allow unauthorized entry. On the other hand, with a facial recognition system, there is no need to worry about unauthorized use. Since all you need is your own body to enter and leave the building, there is no need to worry about inconvenience caused by forgotten passwords or cards, or risk of loss.
(5) Deterrence of unauthorized access
Face recognition systems can accurately log data on who entered and exited a room and when. Therefore, even if a problem occurs within a company or facility, it is possible to quickly identify the cause of the problem. Since the person can be identified immediately, this can deter not only intrusion from the outside, but also internal fraud by employees.
| For a detailed explanation of the Bio-IDiom KAOATO face recognition packaged software, including an overview, what it can do, and the application fields of face recognition, please refer to this page. About Bio-IDiom KAOATO |
|---|
Click here to contact us for more information about face recognition.
6. What are some points to keep in mind about face recognition systems?
Although face recognition systems have many advantages, there are of course some points to keep in mind. The following are some points to keep in mind when considering the introduction of a facial recognition system.
(1) There are large differences in authentication accuracy among products
In general, face recognition systems have a very high level of security, but it is also true that there are differences in performance among products. Some systems do not support changes in facial features over time, while others cannot authenticate people wearing masks. When choosing a face recognition system, it is important to select a product with the highest possible security level.In this regard, NEC Solution Innovator's “Bio-IDiom KAOATO” face recognition package software has a number of identification methods that solve the problem of biometric identification, namely, the risk that the system may fail to authenticate even the person itself. In addition, there are also technologies to deal with the problem of “spoofing” by holding up a photo or image to a facial recognition device, making it possible to configure the device to authenticate only the person himself/herself.
(2) Privacy protection must be taken into consideration
Face-related data handled by facial recognition systems is defined as “personal information” under the Personal Information Protection Law. This means that it must be handled with great care. Specifically, the following actions must be taken thoroughly: “The purpose of use of the data must be notified or announced to the person before taking photographs,” and “The data must not be used beyond the specified purpose of use.
7. What are the applications and usage scenarios for face recognition systems?
Here are eight typical situations in which face recognition systems can be used.
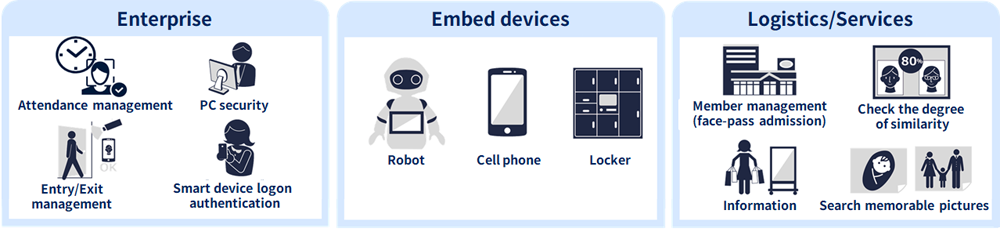
(1) Access control (offices, factories, condominiums)
Face recognition can be used for access control in offices and factories, allowing employees to enter and exit smoothly and hands-free. Face recognition systems also boast a high level of security, making them effective in preventing office break-ins in offices and burglaries in condominiums. As a highly convenient security measure, many buildings are installing these systems.
| * For more information on access control, please click here. Please refer to this page as well. Access control is moving into the era of “contactless” access control! How to choose an access control system that won't fail |
|---|
(2) Payment (retail stores, hotels, restaurants)
Face recognition is also used in “empty-handed payment” systems, whereby users register a photo of themselves in advance, a camera detects them at the payment counter, and payment is made automatically. Users can shop, stay overnight, eat, and drink without cash, allowing them to enjoy sightseeing and shopping with less hassle. The use of this system is spreading to convenience stores, restaurants, and a variety of other venues.
(3) Terminal logon (PC and smartphone)
There are many incidents in the world where PCs and smartphones are operated by third parties and confidential information is stolen. To prevent this, identification using a face recognition system is effective. Using face recognition, the camera built into the terminal can check the face and set the system to prevent anyone other than the person in question from logging on. It is also possible to record the exact working hours with logon history. Thus, face recognition can be used not only as a security measure against information leaks, but also to change the way employees work.
(4) Identity theft prevention (banks, examination halls, event venues)
Tickets for live concerts and performances are increasingly being resold at unfairly high prices. To prevent this, the venue can use a facial recognition system to verify the identity of the person who purchased the ticket, and only the original purchaser can enter the venue. Similarly, exam sites can prevent “dodging” of entrance examinations. It is also possible to prevent “identity theft” at banks.
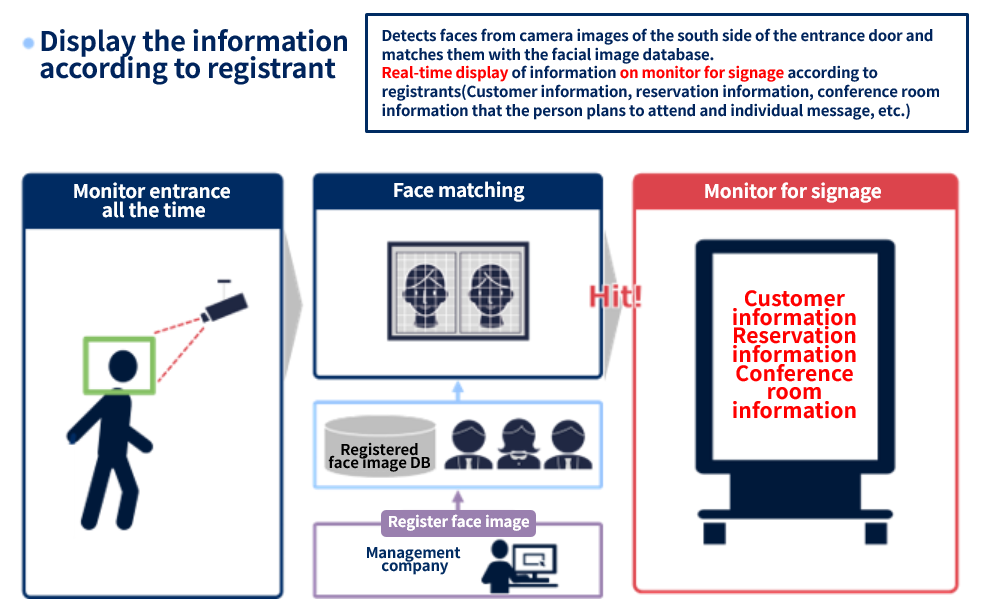
(5) Visitor detection (hotels and stores)
Face recognition systems can also be used to provide generous service to VIP customers. If the customer's information is registered in the database in advance, the camera automatically detects his/her arrival at the store. This allows for quicker service and greater customer satisfaction. This kind of “visitor detection” function is also effective in amusement parks and commercial facilities to help people find lost children smoothly.
(6) Reception (amusement facilities and stores)
At gyms, hotels, etc., there may be waiting time at the reception desk during times when the number of visitors is high. If a face recognition system is introduced, it is possible to instantly recognize a member's face and complete the reception process in a short time. Customers will not only save waiting time, but also enjoy the convenience of being able to visit the store without having to carry their membership card or credit card.
(7) Monitoring (nursing care facilities)
In nursing homes, the safety and health of residents are paramount. If a resident should go out unnoticed, it could lead to an unexpected accident. By installing a facial recognition system and linking it to the cameras in the facility, you can prevent residents from going out without permission. At the same time, it can prevent intrusion from the outside, making the facility safer.
Examples of office, manufacturing, real estate development, and medical applications of face recognition are introduced here. Please take a look.

8. What are the key points in introducing a face recognition system?
So, when you want to introduce a face recognition system, what points should you pay attention to?The following are three major points to consider when introducing a face recognition system.
(1) Select a system with high authentication accuracy and thorough information management
First, choose a system with high authentication accuracy. If the product can withstand checkpoints such as “can it be used to identify people wearing glasses or masks,” “can it be used to authenticate people even if their faces change over time,” and “how low is the false recognition rate,” it can be used long after its introduction. The higher the accuracy of authentication, the higher the level of security and the safer the system can be used.Also, since the data handled is personal information, it is important to check whether the information management is thorough. If the product has features such as “information is encrypted and stored in the database so that it cannot be read from the outside” or “the product can be used stand-alone (without an Internet connection),” it can be used more safely.
(2) Double authentication for even greater security
While a face recognition system by itself is strong enough, it can be combined with another authentication system to further increase the level of security. For example, combining a face recognition system with an IC card (employee ID card) or a face recognition system with a chameleon code (colored barcode) can avoid authentication errors. If you are looking for a more secure and quicker authentication system, “Double Authentication” is the best option for you.
(3) Linking with various systems
Linking a face recognition system with various internal systems will bring more benefits. For example, if a facial recognition system is introduced for access control, it is convenient to link it to an attendance management system. This is because the time spent entering and leaving the office using the facial recognition system can be directly recorded as daily working hours. This eliminates the need for employees to enter their work hours in a spreadsheet every day, or to use time cards to record their arrival and departure times.Facial recognition systems can also be used in a variety of other situations, such as automatic payment at the cafeteria and PC logon management. When introducing the system, consider the various possibilities of use, and you will be able to increase the convenience of the system many times over.
| For a detailed explanation of the Bio-IDiom KAOATO face recognition software package, including an overview, what it can do, and the application fields of face recognition, please refer to this page. About Bio-IDiom KAOATO Here we explain in detail why face recognition is chosen for access control and why Bio-IDiom KAOATO is chosen in particular. The Reason that Face Recognition is Chosen for Access Control Management |
|---|
9. Summary
It is important to choose the best access control system to meet your company's challenges and social conditions. In particular, recently, “non-contact” access control systems, such as facial recognition systems, have been attracting attention in order to reduce the risk of infectious diseases. Since the best system for each company is different, it is a good idea to consult with a specialist when beginning the process of selecting a system. If you have any questions about how to choose an access control system, please feel free to contact us.
The “Bio-IDiom KAOATO” face recognition package software, which is equipped with the world's No. 1* rated face recognition engine and achieves high recognition accuracy, can prevent unauthorized access to and from the office while enhancing convenience.
Click here to contact us for more information about face recognition.
- *
 No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.