Column for Access Control Management and Face Recognition
Access control is moving into the era of “contactless” access control!
How to choose an access control system that won't fail


Breadcrumb navigation
 Table of Contents
Table of Contents
An access control system is a system that prevents unauthorized entry and exit by managing and recording the entry and exit of people. Specifically, there are authentication methods using PINs, IC cards, and biometric information, with “face recognition systems” offering a high level of security and convenience. When choosing a product, we recommend that you select a product that meets the needs of your company.
1. Access control is moving into the era of “contactless” access control! How to choose an access control system that won't fail?
From the standpoint of security, access control systems have become indispensable for offices. Today, we are entering an era in which access control systems are being reconsidered from a new perspective. The new perspective is how to reduce the risk of infection. In an authentication system that requires contact with the equipment, there is a possibility of viruses spreading through the equipment. It makes no sense for a system that is designed to ensure safe corporate activities to increase the risk of virus infection.
In addition, there are many types of access control systems, such as IC cards, fingerprint authentication, and face recognition, and many people may not know how to choose the right one. In this era of the New Normal, we will explain the basics of access control systems that you need to know. Specifically, we will explain “What is an access control system in the first place? What is biometric authentication? What are the key points for choosing an access control system? and “What are the key points in choosing an access control system? Please read it as a guide to make your corporate activities even safer.

2. What is access control?
Access control is to prevent unauthorized access to a building, facility, or room by managing the entry and exit of people. Specifically, cameras and authentication systems are used to identify individuals, and PCs and servers are used to manage entry/exit histories. Software and systems equipped with a series of such access control functions are so-called “access control systems". When you hear the term “access control,” you may associate it with the scene where a person passes through an office entrance by holding up an “entrance pass". In fact, access control is also used in many places other than offices. A typical example is station ticket gates. By reading the data of traffic system IC cards, unauthorized boarding is prevented, and the time spent passing through the ticket gate is recorded on the card.

3. What is the purpose of an access control system?
What does it mean to implement an access control system?
The purpose of an access control system is introduced from two major perspectives.
(1) To enhance security
There are many things in a company that must be strictly controlled. For example, personal information of employees and customers, confidential know-how, cash, and office equipment. If these items were to be stolen by someone, it could lead to a loss of competitiveness and credibility for the company. To avoid the worst case scenario, an access control system can be very effective. For example, an access control system can prevent intruders from entering the office by thoroughly checking the identity of each person who enters and exits the office. Also, by making it impossible for anyone other than those with a specific job title or position to enter a room, it is possible to prevent unauthorized removal of information from the room. Furthermore, by installing a high-performance authentication system, such as fac recognition, it is possible to detect and inform the manager of “co-occupancy,” in which two or more people enter a room at the same time, thereby preventing co-occupancy. By preventing unauthorized entry and exit, you can protect your company's valuable assets.
| * For more information on corporate and factory security measures. Please refer to this page as well. 10 office and factory security measures! |
|---|
(2) To utilize entry/exit recordsIt is not only intruders from the outside that threaten companies.
Sometimes leakage of information or removal of money or goods may occur by the hands of the company's own employees. Access control systems are effective in preventing internal fraud.
Access control systems have the ability to record who enters and leaves a room, when, and in which room, allowing you to immediately identify the person who is causing the problem. It can be said that an access control system can curb fraud. Of course access control data can also be used effectively for purposes other than fraud prevention. For example, by linking an attendance system with an access control system, it is possible to accurately record the attendance time of employees. An access control system can be very useful in understanding the working conditions of employees and creating a comfortable working environment. In addition, access control systems are also effective in preventing infectious diseases. By recording the time employees enter and leave the office and the time they stay in the office, it will be easier to trace the route in case of an outbreak of infection.
4. What are the advantages of using an access control system?
What are the benefits a company can receive by implementing an access control system?
Here we introduce the benefits of access control systems from four major perspectives.
(1) Avoiding the risk of information leaks
One of the items that companies must strictly manage is the personal information of their employees and customers. The Personal Information Protection Law stipulates that “necessary and appropriate measures must be taken for the safe management of personal data,” and in the event of an information leak, criminal penalties and even civil damages may result. Nowadays, a lot of information is stored in a single company PC, and it must be thoroughly managed. That is why it is important to use an access control system to prevent intrusion from the outside and internal fraud. The introduction of an access control system can be considered an “investment” to protect the company's credibility.

(2) Reduce security costs
Many companies hire security companies to take security measures and assign security staff. Of course, direct confirmation by human eyes is very effective in preventing fraud. On the other hand, however, it is also true that it costs a lot of money. With an access control system, there is no labor cost because the system automatically checks who is passing through. In the long run, it is a great advantage to reduce security costs.
(3) Streamlining attendance management
Attendance management is always a problem. For example, employees may falsely record their overtime hours to make them appear less than they are, or conversely, they may increase their overtime hours to increase their overtime pay. It is also time-consuming for the general affairs and labor affairs departments to investigate and reconcile these figures. Therefore, by introducing an access control system to accurately record arrival and departure times, attendance management can be streamlined. This also eliminates the need for “fake” time stamping, which saves time and effort in cross-checking. Employees no longer need to punch in their time cards or enter numbers into the company's system every day, making it extremely efficient.
(4) Infection Control
An access control system will allow you to know “who was in the office, where they were, and for how long. Therefore, in the unlikely event of an outbreak of an infectious disease, it is possible to check the entry/exit history based on the registered facial information and identify the employees who entered and left the office at the same time as the subject. Having a system that allows retrieval of employee access records in this manner will minimize the period of business shutdown.
(5) Disaster Preparedness
Access control systems are actually very effective in the event of a disaster.
When a fire breaks out in an office building, it is difficult to know exactly who is left behind. However, if you have an access control system in place, you can accurately determine who is in which room based on the entry/exit records. This will allow you to quickly determine where to go for rescue. The access control system will also help protect employees in the event of a disaster.
| Please click here for a detailed explanation of the Bio-IDiom KAOATO face recognition software package, including an overview, what it can do, and the fields of application for face recognition. About Bio-IDiom KAOATO |
|---|
Bio-IDiom KAOATO, a face recognition packaged software that is equipped with world's No. 1* rated face recognition engine and achieves high recognition accuracy, can be used for access control in offices and factories. Access control by face recognition can prevent unauthorized access to offices and factories while enhancing convenience.
- *
 No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.
5. What are the different types of access control systems and what are their features?
When it comes to choosing an access control system, there are many different types, and many people are confused. Here are five typical types of access control systems and the advantages and problems associated with each.
| Cost | Convenience | Hygine | Security | |
| PIN Number | 〇 | △ No need to carry, but companies need to take care of forgotten PINs |
△ Contact with numeric keypad |
△ PIN theft, PIN forgetting Cannot prevent tailgating |
|---|---|---|---|---|
| Dedecated IC Card | △ Distribution to each employee is necessary, and reissuance is necessary |
△ Handling of forgotten or lost cards |
〇 | △ Possible unauthorized entry when card is lost, cannot prevent tailgating |
| Traffic System IC Card | 〇 | △ Handling of forgotten or lost cards |
〇 | △ Possible unauthorized entry when card is lost, cannot prevent tailgating |
| Smartphone Applications | △ Possible to introduce at low cost if a company smartphone is available |
△ Handling of forgotten or lost cards and smartphones |
〇 | △ Possible unauthorized entry if lost, cannot prevent unauthorized access, and cannot prevent tailgating |
| Biometric Authentication (Face) | △ nstallation of dedicated equipment such as cameras |
◎ No correspondence due to loss or forgetting Touchless, walk-through available |
〇 | ◎ Prevents unauthorized entry and keeps a camera history |
(1) PIN Number
A PIN-based access control system is a system in which numbers and letters are typed into a numeric keypad to unlock the door. In many cases, it is not possible to record an entry/exit log, and it is a simple, classic system that specializes in authentication only.
Advantages
◎A system that requires only the installation of a dedicated tool at the door, which keeps initial costs low.
◎Easy access to and from workplaces, since there is no need to carry IC cards or employee ID cards.
Problems
▲The PIN number can be intercepted and unlocked, which may allow outsiders to enter the room.
▲Since the user must touch the numeric keypad when authenticating, there is a risk of infection when infectious diseases are prevalent.
▲Employees may not be able to enter or leave a room due to forgotten passwords, and the company will need to take action each time this happens.
(2) Dedicated IC cards (employee ID cards)
IC cards are often used as employee ID cards and are often seen worn around the neck with a strap. They are also sometimes used to authenticate printer and PC to prevent from information leakage.
Advantages
◎Authentication devices can be used to accurately track who enters and exits a room and when, and can also be used for employee attendance control.
◎Reduce the risk of spreading infectious diseases by avoiding contact with the authentication device.
Problems
▲If an employee forgets his/her IC card, he/she will not be able to enter or leave the room, and the company will have to deal with the problem each time.
▲If an IC card is lost, it can be used by an outsider to gain unauthorized access.
▲The loss of an IC card will result in the cost of reissuing a new card.
▲There is also the possibility of intrusion by unauthorized persons due to “shared use” where multiple persons enter and exit a room with a single authentication.
(3) Traffic System IC Card
Access control systems using transportation-related IC cards allow users to enter and exit by holding up a transportation-related IC card, such as Suica or PASMO, to the authentication tool. Unlike a dedicated IC card, the same IC card can be used as is.
Advantages
◎Low installation costs because companies do not need to issue new dedicated IC cards.
◎Authentication is more convenient for employees because they do not need to carry multiple cards.
Problems
▲It is necessary to take countermeasures to prevent access to the room if the card is forgotten or lost.
▲If an IC card is lost, it will cost money to reissue a new card.
▲Anyone with a card can enter and exit the room, which may lead to unauthorized entry.
(4) Smartphone Applications
A smart phone app-based access control system is a system in which doors are unlocked by operating a dedicated app downloaded to a smart phone (hereinafter referred to as “smart phone”). There are two types of systems: one in which the application is held over an authentication tool to enter and exit a room, and the other in which the application is operated remotely to unlock the door (smart lock). Once the application is installed in the company smartphone, it can be used to enter and exit the building.
Advantages
◎No need to install a large scale dedicated system, so installation costs can be kept low.
◎Smartphones are familiar to many people, so employees can use them without stress.
Problems
▲If an employee forgets his/her smartphone, he/she will not be able to enter or leave the room, and the company will need to take action each time.
▲If a smartphone is lost, it can be used by someone else, increasing the possibility of unauthorized entry.
▲It is difficult to use the system if there are many employees who do not use smartphones or if the company has not installed company smartphones.
(5) Biometric Authentication
Access control systems based on biometric authentication (biometric authentication) are now attracting attention as a system that checks a person's innate information, such as fingerprints and face, against registered data to allow entry and exit from a room. There are many types of biometric authentication, including fingerprint, vein, iris, face, and voice authentication, and you can choose the best one for your application and budget.In addition, there is no risk of loss as with a card or smartphone, and “spoofing” is difficult, making this an access control system with an extremely high level of security. For this reason, it is used not only in offices, but also for identification at banks and airports.
Advantages
◎Because you can authenticate with your own body, there is no need to worry about forgetting your card or smartphone and not being able to enter the room.
◎No risk of theft and extremely low risk of forgery, making unauthorized entry more reliable.
◎Because cards and smartphones cannot be lent or borrowed, internal fraud by employees can also be prevented.
Problems
▲Since personal body information is used, data management must be carefully considered.
▲There is a difference between “contact/non-contact” biometric authentication, so care must be taken when selecting a product.
▲The authentication rate is not always 100%, so there are cases where the person cannot be identified at the time of authentication.
▲If a facial recognition system with low authentication accuracy is used, it may be possible to impersonate a person using a photograph.
As described above, biometric authentication is being introduced by many companies due to its high level of security and convenience.
The specific types and advantages are described in detail in the next chapter.
6. What are the types of “biometric authentication systems” that are currently attracting attention, and what are their features?
What are the types of “biometric authentication systems” that are currently attracting attention, and what are their features?
What are the types of biometric authentication systems that are currently attracting attention, and what are their features?Biometric authentication systems offer a very high level of security, covering the problems of conventional access control systems. There are various types of biometric authentication systems, so it is necessary to choose the one that best fits your company's situation and challenges. In this article, we will discuss five typical examples of biometric authentication systems and explain the features of each.
Click here to contact us for more information about face recognition.

(1) Fingerprint Authentication
Fingerprint authentication is a system that authenticates by the stripe pattern of fingerprints. The system reads the fingerprint of the individual, analyzes the points where the pattern is broken (end points) and the points where the pattern diverges (branching points), stores the data, and then matches it with the actual fingerprint held up to a special reader. This is a common authentication method that has been used for a long time among biometric authentication methods.One feature of this method is that the initial cost can be kept relatively low because a dedicated machine for reading fingerprints can be installed at a low cost. On the other hand, it should be noted that some products may not be able to read fingerprints accurately if the finger is shaved off. In addition, since contact with the reader is required, it is important to choose a “non-contact” authentication system if you want to reduce the risk of infection.
(2) Vein authentication
Vein authentication is a system that uses veins in the palm of the hand or inside the fingers for authentication. The veins contain a component called reduced hemoglobin (hemoglobin not bound to oxygen) that reacts to infrared light, from which the vein pattern is read and matched. The major difference between this system and fingerprint authentication is that it authenticates the inside (blood vessels) of the finger, rather than the surface.Vein authentication is characterized by the fact that it is one of the most difficult biometrics to impersonate. It is said that vein patterns are different even between twins, and since the veins are internal to the body, there is no risk of forgery. The data can be used for a long time, as it does not change significantly over time. However, since contact/non-contact varies depending on the product, consideration should be given when introducing the system.
(3) Iris Authentication
Iris recognition is a system of authentication based on the pattern of the iris, the doughnut-shaped part of the eyeball. The pattern of the iris varies from person to person and is said to remain unchanged throughout life. The pattern is not the same even between twins. The iris itself is protected by the cornea, so there is little chance of damage, making it a suitable area for authentication.As with vein authentication, the iris is an internal structure of the body, making it difficult to counterfeit. The pattern is basically unchanged over time, so personal data can be used over the long term. In addition, the risk of infection is reduced because the authentication process is “touchless,” meaning that no contact is made with the device during authentication. However, the cost of installing the system is high because it requires a dedicated authentication system, and there is a possibility that authentication may not be possible if the user is wearing colored contact lenses.
(4) Face Recognition
Face recognition is a system that authenticates individuals based on their facial features. The system takes a picture of the person's face, analyzes and records the positions and contours of the eyes, nose, and mouth as “feature points,” and checks the data against the actual face to confirm that the person is who they say they are. The key point is that the psychological burden on the user is particularly low, since the face is usually used as a means of identifying the other person. Recently, a system has been developed that can authenticate people even when they are wearing masks, and the convenience of face recognition is attracting a great deal of attention.
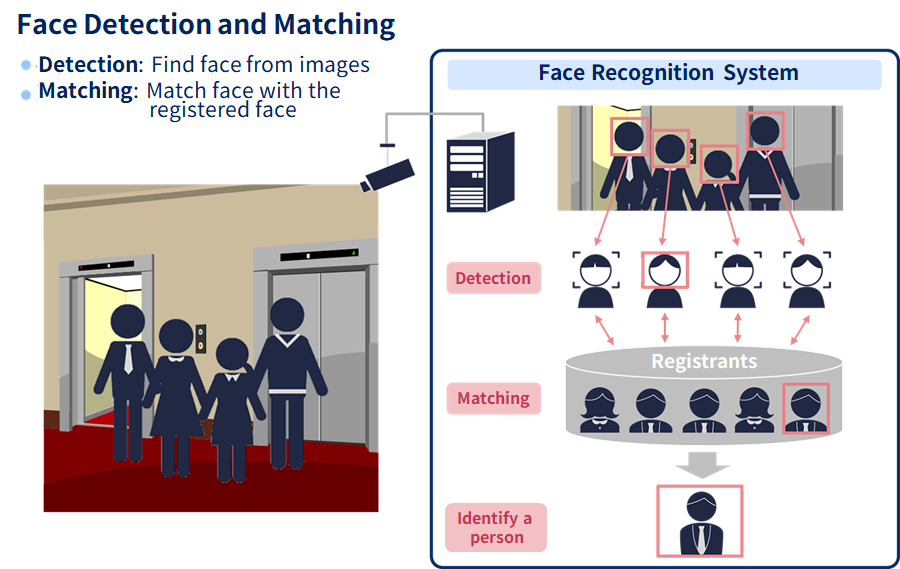
In addition, face recognition systems have various features that can compensate for the shortcomings of other biometric systems. For example, the matching accuracy is extremely high. In the case of NEC's NeoFace face recognition engine, the error rate is as high as 0.5% (the world's No. 1 accuracy rating by the U.S. National Institute of Standards and Technology) even when 12 million still images are authenticated. ), even after 12 million still images are authenticated.
In particular, NEC Solution Innovator's Bio-IDiom KAOATO face recognition package software has a number of identification methods that solve the problem of biometric identification, namely, the risk that even the person in question may be rejected for authentication. In addition, there is also technology to deal with the problem of someone “impersonating” another person by holding a photo or image up to a facial recognition device, making it possible to configure the device so that only the person in question can be authenticated.
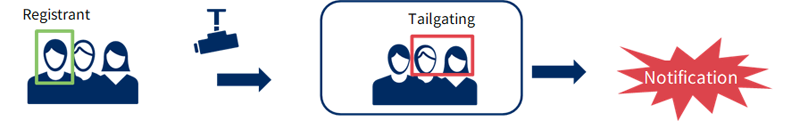
Another attractive feature of this system is that it is touchless, meaning that the user does not have to touch the device during authentication. This reduces the risk of infection to the greatest extent possible, and reduces the burden on employees by allowing them to pass smoothly even when both hands are occupied. Furthermore, since the system recognizes a person's face each time he or she enters a room, it is possible to prevent “co-occupancy,” in which two or more people enter a room at the same time. The advantage of this system is that it is easy to implement in terms of cost, since it requires only a camera and a server and does not require any specialized equipment.
| Face Recognition Packaged Software Bio-IDiom KAOATO, including an overview, what it can do, and areas of application for face recognition, is explained in detail here. About Bio-IDiom KAOATO |
|---|
Click here to contact us for more information about face recognition.
| * Face Recognition System is also explained in detail here. Why is Face Recognition System attracting attention now? Benefits and utilization methods are explained! |
|---|
(5) Voice Authentication
Voice authentication is a system that authenticates individuals by their voices. Each person's voice is like a special “musical instrument,” and the pitch and resonance of the sound differs from person to person. The system takes this data and checks it against the actual voice to confirm whether or not the person is who they say they are. This is a field where research has been progressing recently, and is a technology that is expected to be put to practical use more and more in the future.The feature of this technology is that it recognizes a person's voice, so it can be used to verify a person's identity even over the phone. In addition, as with face recognition and iris recognition, it is non-contact, so the risk of spreading infectious diseases is reduced, and people can smoothly enter and leave a room even if their hands are full.
7. How to Choose an Access Control System and What are the Key Points to Avoid Mistakes?
When it comes time to choose an access control system, what should you look for?
There are four main points to consider when choosing an access control system.
(1) Select a System that Meets Your Company's Needs
The most important thing in choosing an access control system is to select one that is suited to your company's issues.For example, if you have a large number of co-workers who enter a room together at the same time, a facial recognition system with a high level of security would be suitable. If you wish to keep costs as low as possible, you can use a cloud-based access control system that does not require a server. If there is a high level of fraud in a particular room, you can install a high-security authentication tool such as facial recognition only in that room, and use IC card authentication in the other rooms. First, it is important to take stock of the assets to be protected and sort out the issues.
(2) Adapt to the New Normal
Today, we live in an era of “New Normal,” where the risk of infectious diseases is high. Access control systems should be selected that do not risk the spread of infection through the equipment. Facial recognition systems and IC card authentication systems, which do not require contact with the equipment, can be introduced with confidence. It is very important to consider whether or not employees can come to work with peace of mind. If you are not sure which product to choose, we recommend that you consider whether or not the system is contactless as an important factor in your decision.
(3) Linking with Various Systems
Access control systems can be used more conveniently by linking them with various other systems. For example, if the system is linked to an attendance management system, it is possible to accurately record employee work hours. Since the reform of the work style requires the reduction of overtime hours, we recommend that you check whether the product can be linked with a time and attendance system.
(4) Consider the Benefits to Employees
While it is important to consider the benefits to the company, such as “low operating costs” and “no installation work required,” it is also important to consider how much easier it will be for employees to work with the new access control system. For example, “Sales staff often have both hands full with materials and product samples when they come back from their rounds, so let's use a touchless authentication system,” or “Let's consider a biometric authentication system to avoid inconvenience caused by forgotten cards. It is important to choose the most appropriate system based on the way of working at the workplace. If you are conscious of the perspective of “making it easier for employees to work,” you will be able to make a choice that will gain the approval of your employees.
| For a detailed explanation of the Bio-IDiom KAOATO face recognition software package, including an overview, what it can do, and the application fields of face recognition, please refer to this page. About Bio-IDiom KAOATO Here we explain in detail why face recognition is chosen for access control and why Bio-IDiom KAOATO is chosen in particular. Why Face Recognition is Chosen for Access Control |
|---|
8. Summary
It is important to choose the best access control system to meet your company's challenges and social conditions. In particular, recently, “non-contact” access control systems, such as facial recognition systems, have been attracting attention in order to reduce the risk of infectious diseases. Since the best system for each company is different, it is a good idea to consult with a specialist when beginning the process of selecting a system. If you have any questions about how to choose an access control system, please feel free to contact us.
The “Bio-IDiom KAOATO” face recognition package software, which is equipped with the world's No. 1* rated face recognition engine and achieves high recognition accuracy, can prevent unauthorized access to and from the office while enhancing convenience.
- *
 No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.