Columns on Access Control/Face Recognition
What is Security System?
Types and Features for Corporate Users


Breadcrumb navigation
 Table of Contents
Table of Contents
In order for companies to keep their assets safe, they need both technical security to protect networks, systems, etc., and physical security, such as offices. In this article, we will grasp both of these aspects and provide a comprehensive overview of security systems, types, and benefits for corporate managers.
1. What is Security System?
In the first place, a security system is a mechanism to prevent valuable assets from being illegally obtained, tampered with, destroyed, or leaked by external attackers. In the case of a company, the main types of assets are generally "people," "goods," "money," and "information." Security systems can be broadly divided into two categories: technical and physical. Technical security refers to the use of firewalls, anti-virus software, and other devices to digitally prevent attacks on networks, systems, and data. Physical security, on the other hand, is a mechanism that uses security cameras, sensors, security locks, etc. to prevent physical damage to the office.
In order to protect their assets, companies need to take full advantage of both technical and physical security to protect against threats.
2. Security System Relating to Internet
The dangerous outside in technical security is, simply put, the Internet. If internal fraud by employees and stakeholders is overlooked, cyberattacks are essentially carried out over the Internet. Attacks can be used in a wide variety of ways, including malware, email spoofing, phishing sites, and attacks that take advantage of supply chain vulnerabilities.
Especially in recent years, with the spread of cloud services, companies are increasingly placing their systems and data on the Internet (on the cloud), so it is very important to prepare for attacks from the Internet. The following are the main types of security systems related to the Internet.
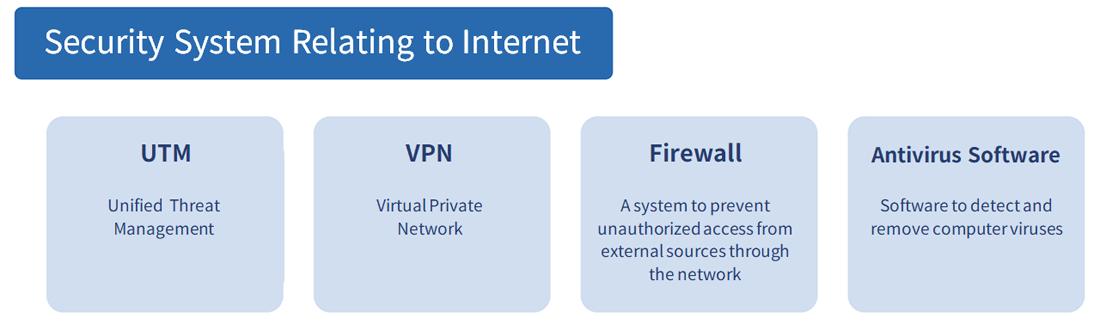
UTM
Uttam is an abbreviation for "Unified Three-Eight Management," which translates to "Unified Threat Management." As the name suggests, Uttam integrates multiple security functions into a single system to prepare for a wide variety of threats. Preventing threats from the Internet requires a variety of security features, but implementing separate solutions for each feature reduces overall security visibility and complexity to manage. In this regard, Uttam can prevent damage from the Internet by various means and improve the efficiency of operations necessary for threat detection and response. Firewalls and anti-virus software, which will be discussed later, are also included in the main functions of Uttam.
VPN
VPN is an abbreviation for "Virtual Private Network", which means "virtual private line" in Japanese. Usually, the Internet connection is shared by multiple people. However, this is like walking down the main street with important documents in your hands, and you are still worried that the traffic (information) sent and received there will be intercepted by an attacker. The function of a VPN can be likened to setting up a virtual tunnel that only certain people can pass through. The appearance of this tunnel is not visible to outsiders. In addition, a VPN also applies a high level of encryption to the traffic that passes through its tunnel, making your information even more confidential.
Recently, with the spread of telework, there are more opportunities to exchange important data on the Internet. In doing so, more and more companies are using VPNs to ensure the safety of their communications.
Firewall
A firewall is a system that prevents unauthorized access from the outside through the network. Firewalls sit at the boundary between external and internal networks, acting as walls and gatekeepers against external threats. The basic function of a firewall is to look at the IP address of the traffic that is trying to access the inside, and check whether the traffic is allowed in advance. It is particularly fundamental in technical security to block external attacks.
Antivirus Software
Antivirus software is software that detects and removes computer viruses that damage your system and data. Once infected, the damage can spread to other systems and devices via the network, so countermeasures against viruses are essential. There are various types of viruses, such as "Trojan horses," "worms," and "ransomware." Each of these effects is also diverse, such as creating a backdoor to infiltrate the network, falsifying data, and leaking it to the outside. Some of them even lock the system itself, rendering it unusable or destroying it.
Viruses are constantly evolving, so it's important to regularly update your antivirus software to keep up with the latest threats.
3. Physical Security System
Physical security systems must prevent unauthorized entry into offices and critical facilities, and provide mechanisms to protect employees, information, cash, hardware, and other assets. No matter how robust the security tools and technical security measures, there is still a risk of important information being leaked if someone physically enters the office and steals materials or devices, or if a wiretap or hidden camera is planted. In the first place, allowing such an unauthorized intrusion is itself a major risk to the company and its employees. Therefore, it is essential for companies to have a strong security system, both physically and in terms of risk management.
Security Camera Systems
Security cameras can be installed to record and monitor external intrusions and internal irregularities. The main locations where security cameras are installed include building entrances and exits and important rooms and facilities. By utilizing security cameras, if some trouble occurs, the video recordings can be referred to and it can be quickly confirmed who did what, by what means, and by what means. In addition, by making it possible to monitor the images from all security cameras in real time and centrally in the security office, guards can monitor multiple locations without having to walk around from place to place. This helps to reduce the burden on security guards and to save on labor costs by reducing the number of security personnel. An additional point is that the very presence of security cameras can be a deterrent to criminal activity.
Electronic Lock Systems
Electronic lock system is a system that uses a PIN number, IC card, fingerprint, or other biometric information as a key to restrict access to a person. Unlike physical locks, there is no need to worry about loss or theft, especially if a PIN or biometric data is used as a key. Many electronic lock systems can also capture a record of locks opened and unlocked, so they can be used to check who entered and left, when, and how they entered and left, and can be used as a substitute for attendance records or to check the status of problems that may occur. In addition, the system can be used as an anti-picking measure, thus increasing the overall level of security. Access Control SystemsAn access control system is a security solution that allows you to control who enters and exits your office, when, and where. By utilizing the security cameras and electronic locks (authentication systems) introduced above, it is possible to restrict access to rooms and compartments to specific people, while at the same time obtaining records of their entry and exit. In addition to reducing the risk of external intrusion and internal fraud, access control systems can also be used to cut costs by reducing the number of security guards and to control employee attendance.
4. Enhanced Security for Access Control System! Face Recognition Packaged Software Bio-IDiom KAOATO
If you are looking for an access control system to enhance security, we recommend you install the Bio-IDiom KAOATO face recognition software, which can quickly and accurately match the face of a person trying to enter or leave a room with that of a person registered in the system in advance, preventing unauthorized entry and realizing non-contact lock opening. This enables prevention of unauthorized entry and contactless opening of locks. The features and advantages of Bio-IDiom KAOATO are explained below.

Highly Effective in Deterring Fraud
Bio-IDiom KAOATO can accurately distinguish human faces using NEC's high-precision face recognition engine. This prevents the intrusion of people who are not registered in the database. It is also possible to log and check information such as who entered and left the room and when. This can be expected to have a deterrent effect not only against external intrusions but also against internal fraud.
It can be used without burden
There are many different types of biometrics, such as fingerprints, veins, voice, and iris. However, authentication by these methods requires a specific action, such as "holding a finger over the terminal", and the bottleneck is that it causes the user a considerable amount of time. On the other hand, face recognition by Bio-IDiom KAOATO can be completed quickly without the need for special operations. Judging who the other person is by their face is something that humans experience on a daily basis, so it is possible to suppress psychological resistance.
No Need for Contact
Bio-IDiom KAOATO is a system that utilizes face recognition, so there is no manual operation process. This makes it possible to realize non-contact access control, and it can be used hygienically even in the event of an epidemic of infectious diseases such as the new coronavirus.
No need for Specialized Equipment
If you want to use a fingerprint or iris as a biometric key, you need a special specialized device. However, Bio-IDiom KAOATO can also be used with general webcams, etc., so the cost of introducing a new dedicated device can be reduced. In addition, since existing face photos can be repurposed for the face data to be collated, the time and effort required to register face data is reduced.
|
|---|
5. Installation Benefits of Security System
Improving security is a key challenge for every company. By implementing a security system, you can expect the following benefits:
Able to Defend Against External Attacks
Businesses have a variety of assets that are attractive to attackers. Implementing a security system can help you better prepare for cyber and physical attacks and make it easier to protect those critical assets. Even if the damage cannot be reduced to zero, the security system can detect abnormalities at an early stage and quickly check the situation, making it easier to reduce the spread of damage.
Prevent Information Leakage Outside the Company
As shown in the above merits, the introduction of a security system technically and physically makes it easier to prevent attacks from the outside, making it easier to prevent confidential information such as personal information from leaking outside the company. Security systems can also help curb not only external attacks, but also insider fraud threats.
For example, if you restrict access to important files, or install access control systems and security cameras in reference rooms, it will be difficult for even employees to take important information without permission. In the unlikely event that something goes wrong, you can check the logs to see who accessed it, so you can quickly identify which route the information leak originated from.
Enhance Social Credibility
The information held by the company also includes data related to external stakeholders, such as personal information of customers and transaction data with affiliated companies. Building strong security is also important to protect the rights and interests of these stakeholders. If you can gain a social reputation as a company with solid security management, it will be easier for people to consider contracts and other matters in a positive way.
In order for companies to keep their assets safe, it is important to increase security both technically and physically. For companies that want to improve physical security, we recommend installing an access control system using the face recognition software "Bio-IDiom KAOATO".
“Bio-IDiom KAOATO” performs facerecognition upon entry, preventing unauthorized access and enabling contactless door unlocking. It is a facial recognition package software equipped with an industry-leading facial recognition engine, achieving high authentication accuracy.
6. Summary
In this article, we have provided an overview of security systems and the basic types of security systems from both technical and physical perspectives. There are many ways to protect against external attacks. In order to protect your valuable assets, why not check your company's security system again and work to strengthen it?
