Columns on Access Control/Face Recognition
What is the measure to prevent tailgating?
Introducing Access Control System


Breadcrumb navigation
 Table of Contents
Table of Contents
In order to prevent the risk of information leakage, it is effective to take measures such as installing security gates, cameras, and introducing anti-passbacks. In this article, we will explain these features and the main authentication methods used for access control, and also introduce the recommended face recognition system for anti-occupancy measures.
1. What is Tailgating?
Tailgating is the act of a person who is restricted from entering the room together when the person who is allowed to enter the room opens the door or gate. There are two types of accompaniment: when the person who has permission to enter the room intentionally invites a third party, and when a person who does not have permission enters the room without permission.
Since there is a risk of information leakage and system manipulation of the company, companies are required to take thorough measures to prevent tailgating.
2. The Three Anti-tailgating Measures and Their Advantages and Disadvantages
The three countermeasures including "Install Security Gate", "Use Anti-Passback" and "Set Camera" are effective for prevention of tailgating.
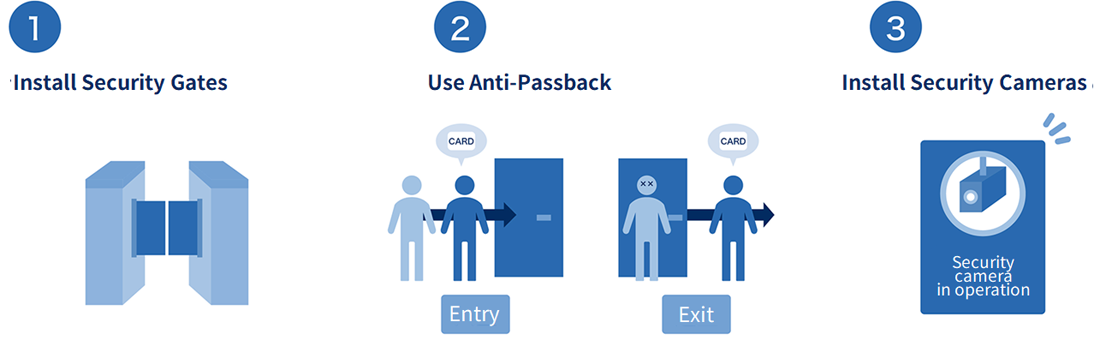
(1) Installing Security Gates
A security gate allows only authorized persons through an authentication system such as biometric authentication or IC cards. There are two main types of security gates: flapper type and arm type. The flapper type is a system in which a plate-like part called a flap opens after authentication to allow entry, and can be easily understood by imagining an automatic ticket gate at a train station. The arm type, on the other hand, allows entry by rotating the arm one by one after authentication, and is generally used in amusement facilities.
Advantages of Installing Security Gates
The advantage of installing security gates is that they can be reliably checked one at a time. With the flapper type, the flap opens when an entrant is authenticated, and the flap closes again when the entrant passes through. Therefore, compared to doors that allow multiple people to enter at once, security gates can prevent people from sharing a room because they reliably authenticate one person at a time.Security gates are also more efficient and save on labor costs by eliminating the need for multiple security guards on a 24/7 basis. Furthermore, visitors are familiar with the system, making it easy for them to know when they are entering or leaving the building.
Disadvantage of Installing Security Gates
There are three disadvantages of security gates. Secondly, security gates are devices that operate on electricity. Therefore, in the event of a power failure due to an earthquake or lightning strike, the gate may not be able to be restored quickly enough to prevent outsiders from entering.The third disadvantage is that security gates cannot completely prevent co-occupants. This is because most security gates use an IC card for authentication, so if an outsider uses the IC card, he or she can pass through the gate. Therefore, if you want to use security gates to prevent people from being taken together, you need to incorporate a system that compensates for the weak points of security gates, such as biometric authentication and security cameras.
(2) Use Anti-Passback
Anti-passback does not allow a person to leave a room unless the authentication record at the time of entry can be confirmed. This reduces the risk of information leaks, etc., because even if a suspicious person successfully enters the room with a companion, he or she cannot leave.
Also, with anti-passback, even if the person entering the room somehow gives his/her authentication card to an outsider outside, if there is a discrepancy with the authentication record, the outsider cannot enter the room.
Advantages of Anti-Passback
Advantages of Anti-PassbackThe advantage of anti-passback is that it does not cost any equipment. Depending on the manufacturer, anti-passback is often a standard feature of access control systems, and since nothing is required other than an authentication reader, companies can take measures against co-travelers at low cost.
Disadvantages of Anti-Passback
Similar to security gates, anti-passback cannot completely prevent tailgating. Anti-Passback prevents outsiders from leaving the room.Tailgating is possible if an authorized authenticator enters the room together with an authorized authenticator when the door or gate is opened, and leaves the room together with the authorized authenticator. Although Anti-Passback makes outsiders feel psychological resistance to the idea that they cannot leave the building if they illegally enter, the system does not actually always prevent tailgating.
(3) Installing Security Camera
Installing cameras allows you to store video evidence of co-occupancy. Remote monitoring is also possible, so various locations can be monitored from a single location, and alarms can be used to notify the office of any co-occupancy. Recently, cameras equipped with facial recognition systems have been introduced to provide higher security measures.
Advantages of Installing Security Camera
The advantage of installing cameras is that recorded data can be saved and used as evidence in case of trouble. The mere presence of a camera can make outsiders or suspicious persons aware that they are being watched, which can be a deterrent to crime. The same is true for employees, who can expect to deter power harassment and misconduct within the company and improve morale and business operations because cameras are monitoring the company.
Disadvantage of Installing Security Camera
Installing cameras is not illegal in itself, but there is a risk of invasion of privacy if the recorded data is saved, so care must be taken in handling them. Especially in the case of Internet-based cameras, there is a risk of unauthorized access, malware infection, and tampering. In addition, some cameras may not be able to authenticate properly when there are a large number of people passing through, such as during busy times when people are arriving at or leaving work.3. What Authentication Methods are Used for Access Control?
There are three main authentication methods used for access control as a measure to prevent people from sharing a room: PIN, IC card authentication, and biometric authentication. The characteristics of each are as follows.
PIN
PIN is a system that allows entry by entering a set number into a device attached to the door. This recognition method can be installed at low cost, since the dedicated device is simply attached to the door. In addition, there is no need to worry about losing the IC card used for authentication, since the PIN is all that is required to authenticate.However, if the PIN is leaked outside the company, even outsiders can easily enter the room. In addition, it is not a good measure to prevent people from entering the office together, since an outsider can enter the office while the door is open after an employee has entered his/her PIN.
Authentication by IC Card
This method allows employees to enter and exit by inserting or holding up their employee ID card or transportation system IC card in a dedicated device. Compared to biometric authentication, the introduction cost is lower, and the non-contact recognition is more hygienic. In addition to access control, the IC card can also be used for authentication when using computers, printers, and other devices, increasing convenience.
However, the use of IC cards for authentication does not prevent people from entering a room together, since outsiders can enter when the door is opened. There is also the risk of losing, forgetting, or having the IC card stolen, and if IC cards are lent or borrowed among employees, the individual cannot be identified and there is a risk of identity theft.
Biometric Authentication
Biometric authentication is an authentication method that uses physical characteristics such as face, fingerprints, and veins. Since authentication is based on biometric information possessed only by the individual, it is characterized by a higher level of security than authentication methods using passwords or IC cards. For example, in fingerprint authentication, a fingerprint is read by a dedicated device and matched with registered data to confirm the individual's identity. Since the biometric information is unique for each individual, it can be used to prevent identity theft, and unlike IC card authentication, there is no need to worry about it being stolen, forged, or inadvertently lost. Biometric authentication is also highly convenient because the user himself or herself is the key to authentication.However, biometric authentication is not 100% accurate. Some systems may not be able to cope with changes in facial and fingerprints over time, and authentication may fail. When choosing a biometric system, the accuracy of the authentication is an important point. One objective test to determine this is the face recognition technology benchmark test (FRVT Ongoing) conducted by the National Institute of Standards and Technology (NIST), and NEC's face recognition technology has been ranked first in the world in this test multiple times. NEC's face recognition technology is also capable of updating face recognition data each time it performs authentication, making it suitable for use over time, and is highly evaluated by customers for its convenience.
The Bio-IDiom KAOATO face recognition package software, which is equipped with the world's No. 1* rated face recognition engine and achieves high recognition accuracy, can be used for access control in offices and factories. Access control by face recognition can prevent unauthorized access to offices and factories while enhancing convenience.
- *
 No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.
4. Face Recognition System is Recommended to Prevent Tailgating
Among various biometric authentication methods such as face, fingerprint, and vein, a face recognition system with a high level of security is particularly effective in preventing people from being brought together. Face recognition systems are particularly effective in preventing people from entering a room together, as they can easily detect outsiders even when two or more people enter the room together. Unlike IC card authentication, there is no need to worry about forgetting or losing the card, and unlike fingerprint authentication, this non-contact authentication system reduces the risk of infection and is hygienic.
Furthermore, NEC Solution Innovator's “Bio-IDiom KAOATO Face Recognition Access Control System” uses “walk-through face recognition” to authenticate users while they are walking without stopping, allowing smooth entry and exit even when both hands are full. In addition, since a record of the entrance and exit is kept in the form of a face screen log, it is easy for the administrator to identify the person entering the room and to manage the entry/exit records.
The Reason that Face Recognition is chosen for Access Control
Here is a detailed explanation of why face recognition is chosen for access control, and why Bio-IDiom KAOATO is chosen among them. Please take a look.
5. Summary
While security gates, cameras, and anti-passback systems are available, a face recognition system is recommended for preventing shared access at a high security level. In particular, NEC Solution Innovator's “Bio-IDiom KAOATO Face Recognition Access Control System” is a highly secure access control system that is easy to use for both employees (users) and managers. If you are considering the introduction of an access control system or feel that your existing access control system is not up to the task, why not consider NEC Solution Innovator's face recognition system?
