What is Bio-IDiom KAOATO?
NEC Solution Innovator is committed to every step of the face recognition process. Functions that thoroughly analyze UX (customer experience) and realize highly available access control and privacy-friendly operation and management functions are now available in Bio-IDiom KAOATO 6.0 installed and enhanced.


Breadcrumb navigation
 What is Bio-IDiom KAOATO?
What is Bio-IDiom KAOATO?
Bio-IDiom KAOATO is a face recognition package software equipped with NEC's face recognition engine NeoFace.
Face recognition authenticates by matching the image of the person stored in the database with the face image of the target person taken with a camera. It is secure because it is difficult to spoof, and there is no need to have a physical key or IC card, or set a password. It is also effective in improving operational efficiency by reducing security risks due to loss or theft and eliminating the hassle of reissuance.
NeoFace has achieved the world's No. 1* rated authentication accuracy. We have a track record of operation in more than 1,500 systems in Japan and overseas, such as access control.
- *
 No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.
 Features of Face Recognition
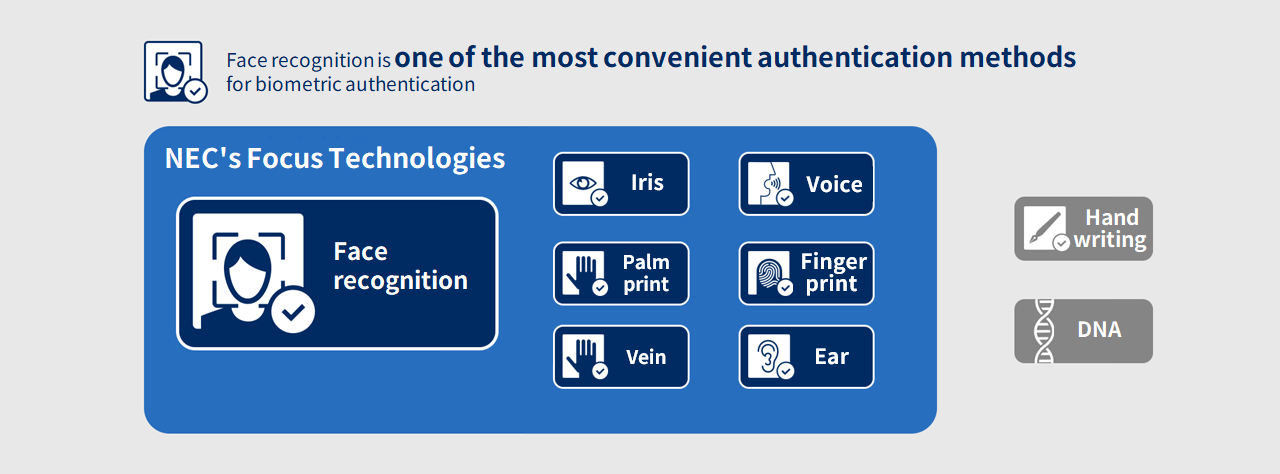
Features of Face Recognition
Face recognition is one of the most convenient authentication methods for biometric authentication.
1. Natural authentication
The face is a familiar authentication method that humans usually use as a means of identifying the other person, and the psychological burden on the user is low.
2. Non-contact/Non-binding
Since there is no need to hold a finger over it, it is possible to perform highly convenient authentication without forcing special operations.
3. High cheating suppression effect
It is also possible for the administrator to visually check the face at the time of verification, such as leaving a face image log, and a high fraud suppression effect can be expected.
4. No exclusive device needed
A general Web camera can also be used., and an existing face photo can also be used as registration data, so there is no need for a dedicated device.
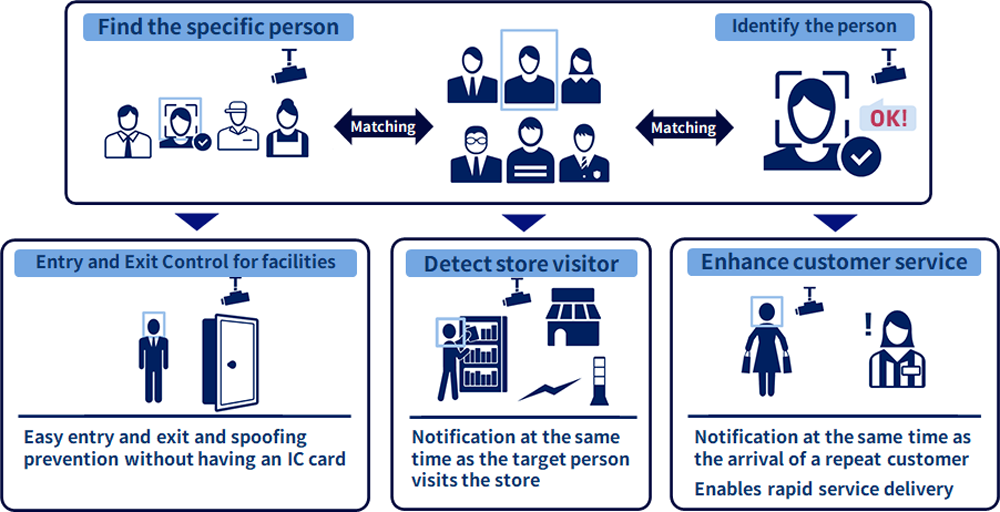
 Examples of application areas of face recognition
Examples of application areas of face recognition
Usable a wide range of applications, from security enhancement to service sophistication.
 Why "KAOATO" is chosen?
Why "KAOATO" is chosen?
Functions that match customer needs and high-precision face recognition based on a wealth of experience have achieved ease of use and a high level of reliability.
| Features | Descriptions | Value provided |
| Face recognition technology with high accuracy |
|
|
|---|---|---|
| Abandoned implementation cases |
|
|
| System scalability |
|
|
| Useful functions for operation |
|
|
- *NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.
 What you can do with the latest Bio-IDiom KAOATO 6.0
What you can do with the latest Bio-IDiom KAOATO 6.0
1. Identify fraud with behavioral biometric detection
Usage scene: Entering and exiting condominiums and offices
In unauthorized use by holding up a photo or smartphone, if the auto-lock of an apartment building is opened by unauthorized use, there is a possibility of intrusion by outsiders or burglary damage, which could threaten the safety of residents. There are ways to prevent unauthorized use by spoofing, such as using a 3D camera to measure depth or turning to the side. However, these functions are not optimal for situations where authentication is required while walking or when multiple people need to be authenticated at the same time, such as when an apartment building is auto-locked, and the convenience of face recognition is reduced.
Bio-IDiom KAOATO's biometric detection function by behavior to detect fraud
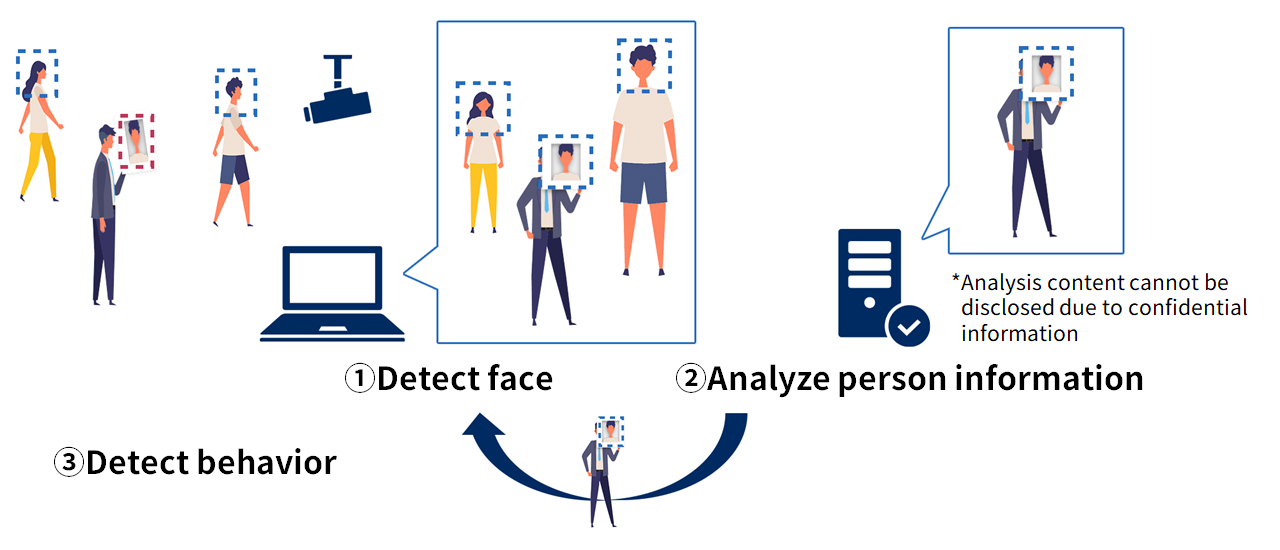
Bio-IDiom KAOATO has a behavior detection function (patent pending) that enables face recognition while walking without standing still, enabling walk-through and simultaneous multiple-person authentication to enter and exit a room. With this function, AI detects movement, surface temperature, and other factors to determine if there is any irregularity. For example, by detecting the movement of a person attempting to pass through by holding up a face photo, the AI can determine that the movement is unauthorized and prevent the door from being unlocked, thereby preventing unauthorized entry. Since it is possible to authenticate multiple people at the same time while walking, the system can be implemented in places with a large number of people entering and exiting. Other applications include detecting the corner of the eyes without standing still and checking the temperature with a thermal sensor, thereby restricting entry to those who are deemed hotter than the value set by the customer.
The system contributes to ensuring safety and security in offices, security zones, hospitals, schools, factories, and other situations where access control is required to improve security without reducing convenience.

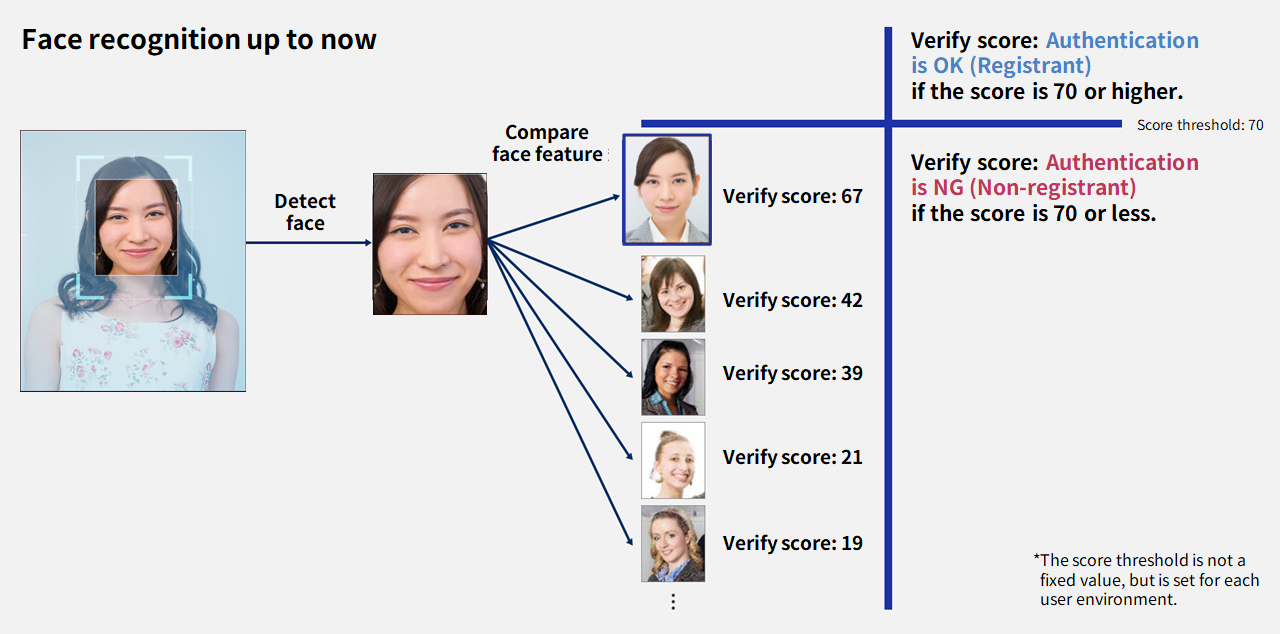
2. Multi-step authentication reduces operational burden and supports user authentication
Use case: To reduce the operation and management burden and to perform highly accurate face recognition
Face recognition is a highly convenient authentication method because it allows users to authenticate without holding anything in their hands. Face recognition enables users to experience “safe, secure, easy-to-use, and smooth authentication,” such as entering and exiting a factory while carrying a load or reducing the number of personnel by unattended reception at a hospital. In order to perform face recognition with a high degree of accuracy, the camera must be installed in a position that takes into account the exposure to the sun and fluorescent light. However, there are also issues such as the inability to install the camera in a position with good conditions depending on the installation environment and location. In such cases, authentication errors are more likely to occur, which may increase the operational load.

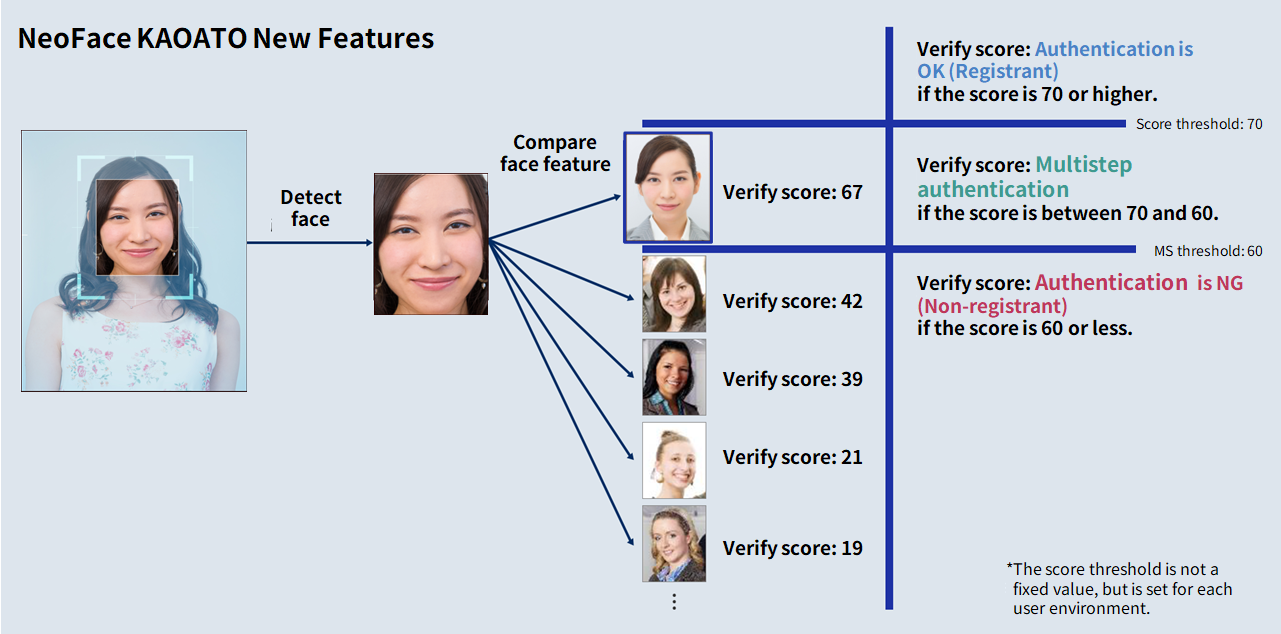
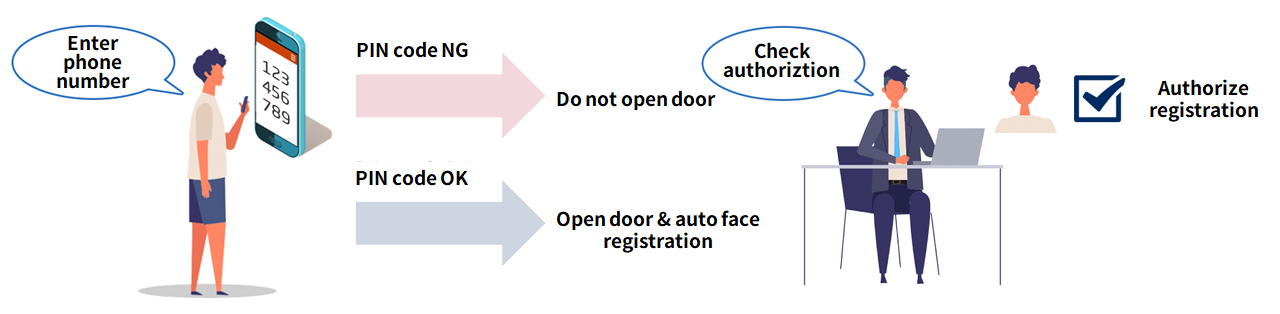
If the matching score is not sufficient to authenticate the user as a registered user, multi-step authentication is performed, and the user's unique PIN code is entered, allowing entry and exit even when facel recognition fails. In addition, the system is designed to prevent security risks from malicious acts, since the system does not perform identity verification if the matching score is low. The system also has a function that automatically registers additional (unauthorized) face images when the user's identity verification operation is performed, so that the next time authentication is performed, the authentication score improves and the user can enter and leave the room using only face recognition. Since face images can be registered for each environment, the more the system is used, the more the authentication rate improves, resulting in a non-stop, highly convenient entry/exit experience.
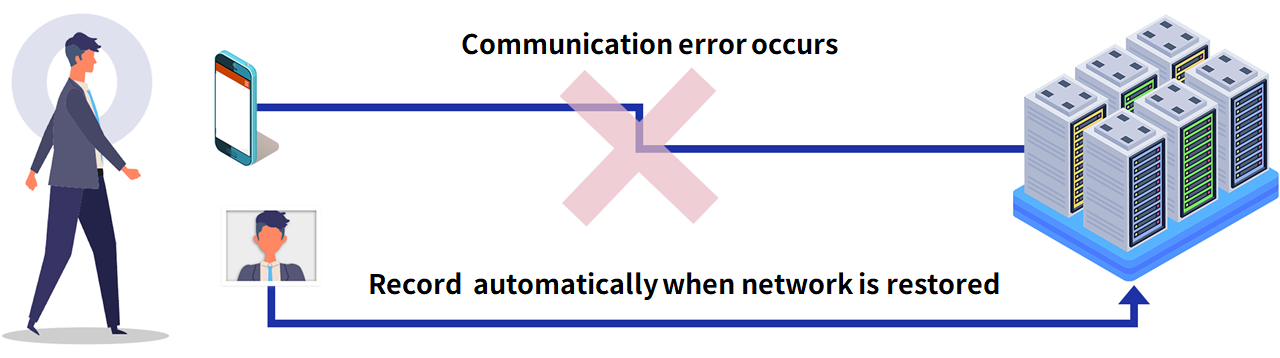
3. Offline authentication and health check functions support continuous operation
Use case: To keep authentication running even in the event of a network failure
In addition to authentication errors, HW failures and network failures can also occur when facial recognition fails. If communication between the server and client becomes impossible, the access control system cannot continue to be used and may be suspended until the system is restored. Even if the database information on the server cannot be accessed, operation can be continued using the information securely stored on the installed terminals, thus minimizing problems such as inability to enter or exit a room or to keep records. During communication failures, facial recognition record data is also temporarily stored in the installed terminal and transferred to the database information upon restoration, so that no authentication records (logs) are lost. In addition to communication and HW failures, the system has a health check function that automatically restores the system even if the face recognition application itself terminates abnormally, thereby supporting high availability of the system.
4. Flexible entry and exit control according to the customer's operation
Use case: Usage scenarios where holidays vary by user In office buildings and factories
There are situations where employees are not allowed to enter or leave on holidays or special days, and only some contractors or employees are allowed to enter or leave for building or elevator maintenance work. In such cases, if employees are allowed to enter and leave the building using facial recognition as usual, this could lead to problems, incidents, or accidents.
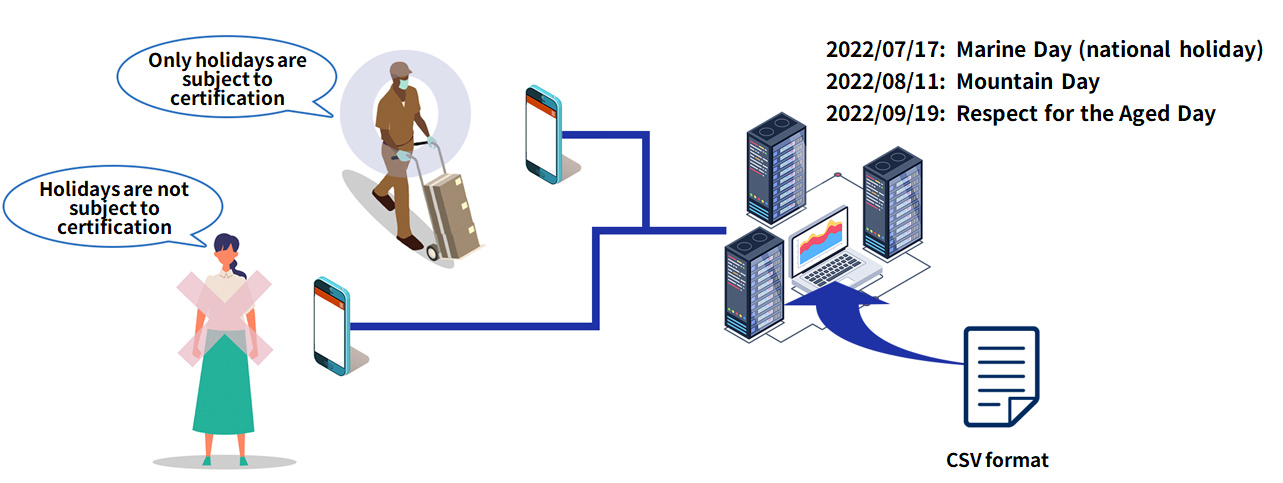
In addition to stopping facial recognition on specified days of the week, the system can also be used to accommodate users' own schedules, such as special holidays for users.
User-specified holidays can be set in the “National Holidays” format provided by the Cabinet Office, allowing easy batch importing of holidays.
5. Integration with NEC/third-party hardware and software
KAOATO can be connected to various hardware and software. Please contact us for more details. Please contact us for more information about other connectable devices.
6. Masking reflections on uncontrolled premises, etc., reduces the hurdle of installing cameras
Use Case: To reduce hurdles to camera installation
When a camera needs to be installed in a location where uncontrolled areas can be seen, or in a production plant where confidential information is to be displayed, it is possible to mask the areas where the camera will be seen.
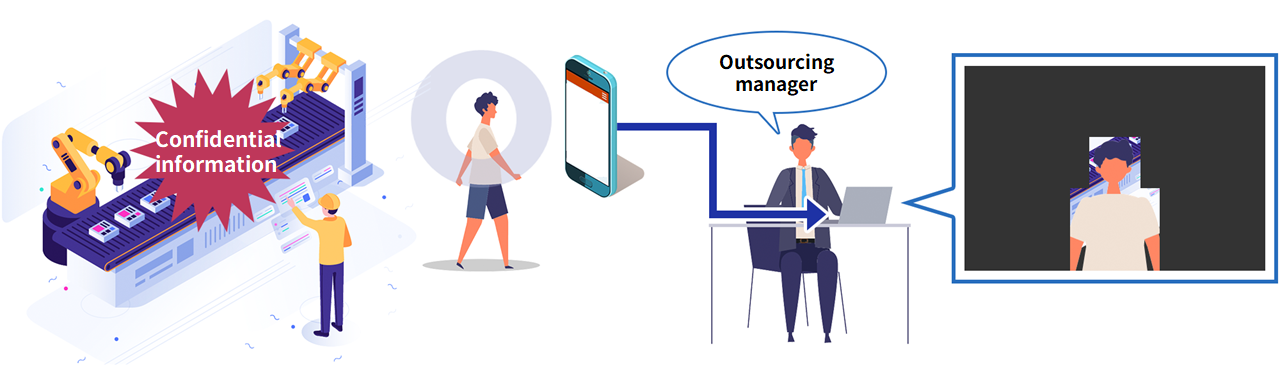
By masking the background except for the person, the administrator can see only the user's authentication results.
Hiding confidential information can be expected to reduce the psychological burden of information management.
In addition, a function that allows only more authorized administrators to view images is being designed to handle situations where images with masking removed are displayed. (To be implemented in the future)