Column for Access Control Management and Face Recognition
What is importance of office security?
Introducing key points and countermeasures


Breadcrumb navigation
 Table of Contents
Table of Contents
Office security is an important measure to protect your company's assets and trust. This article explains the importance of office security, key points in office security measures, and specific countermeasures.
1. What is Office Security?
Office security is a measure to protect a company's assets and ensure smooth business operations.
Offices store many items of monetary value such as cash, checks, and computers, and employees work there every day as human assets. Office security measures are essential to protect these assets.In recent years, companies have also been holding a lot of information assets such as customer information, personnel information, and financial information. If these information assets are leaked, not only will the company be labeled as one that fails to comply with laws such as the Act on the Protection of Personal Information, but it will also cause significant losses to management. Furthermore, the revised Personal Information Protection Law, which went into effect on April 1, 2022, has added additional responsibilities and strengthened penalties for businesses that handle personal information. Therefore, it is imperative that companies with inadequate office security take thorough measures to protect personal information.
Another factor that has increased the importance of office security is the growing number of cyber crimes in Japan in which confidential information is stolen or misused through unauthorized access to company networks. According to the “Economic Crime Survey 2020 (Japan Analysis)” compiled by the PwC Japan Group, a global consulting firm, cybercrime is the number one economic crime and fraud that Japanese companies have encountered in the past two years. This situation calls for companies to take thorough office security measures.
2. Main Risks in Office Security
The first thing you need to know when implementing security measures is the risks that can occur in your office. The three main risks are as follows.
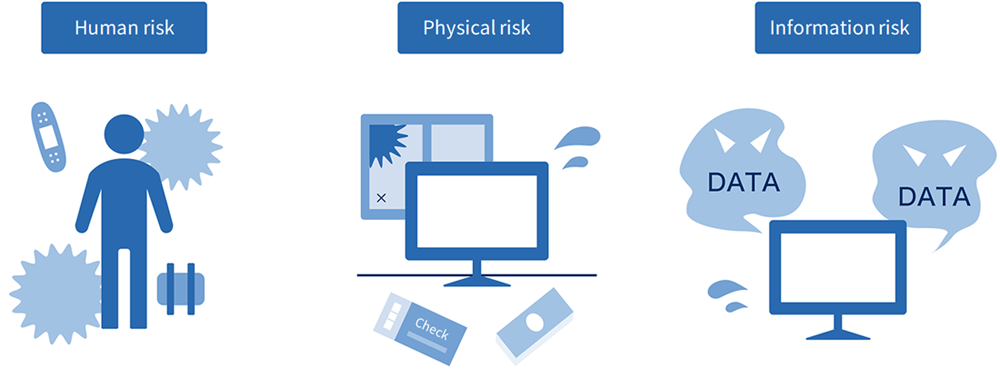
Human Risk
"Human risk"refers to the risk to the physical safety of the people in the office, including employees and management. If office security is not adequate, a suspicious person may enter the office and injure an employee or manager. To avoid such risks as much as possible, it is essential to take security measures to prevent suspicious persons from entering the office. Specifically, it is effective to install a high-security authentication system at entrances and exits.
Physical Risk
"Physical risk "refers to the risk associated with the monetary value of the goods in the office. There are many items of monetary value in an office, such as cash, checks, computers, office furniture, employee valuables, etc., and there is always the possibility that they may be stolen. In the unlikely event of a burglary, office windows and equipment may be broken, and thorough office security measures are essential to prevent such various types of damage.In addition to theft, companies may also experience tampering with company vehicles or damage to infrastructure equipment. In addition, consider the possibility that earthquakes, fires, and other disasters may cause damage to buildings and loss of documents in the office.
Information Risk
"Information risk” refers to risks related to data leaks and information leaks. While data can be leaked due to external system attacks, such as the aforementioned cybercrime, information can also be easily leaked through employee computer mishandling or by taking documents home with them. In addition, peeping into computers or eavesdropping on meetings by visitors can also lead to information leaks. To prevent such risks, it is necessary not only to implement office security measures but also to thoroughly educate employees on information management.
3. Key Points of Office Security Countermeasures
Office security measures do not work by simply installing a high-security system. It is important to raise employee awareness of security and introduce security measures that match the company's issues and objectives. Raise employee awarenessThe main causes of information and data leaks are loss, misplacing, misdirection, and mismanagement of computers and data by employees.
Enhance Employee's Awareness
To prevent information leaks due to such human error, ensure thorough education and training on information security within the organization. In addition, it is important to create manuals for handling information management, establish security rules, define measures in case of information leaks, and share them within the organization to raise employee awareness.
Visualize Assets then Grasp Issues and Countermeasures
Visualize assets and understand issues and countermeasuresIn order to implement office security measures suited to your company, it is important to understand the current status of your company's assets and identify whether there are any management issues. Since information assets are particularly difficult to see, it is desirable to visualize them. Information assets in a company can include the following.
- Customer Information
- Employee Personal Information
- Product Development Information
- Technical Information
- Financial Information
- Data on computers and USB memory stick
- Data on servers or cloud services
- Data on paper media, etc.
Check where these information assets are, who is responsible for them, and how they are managed. When managing information assets, it is recommended to use an information asset management ledger. An information asset management ledger is a ledger in which information assets are managed by entering information about users, storage locations, confidentiality, etc., making it easier to keep track of information assets.
Then, based on the issues revealed by visualizing these information, consider security measures that suit your company. For example, if you find an issue that “there is no record of visitor information and it cannot be checked in case of emergency,” you can decide to introduce security systems and tools such as “installing security cameras” and “creating IC cards for visitors to record their entry and exit,” according to your company's scale and budget.
4. Detailed Office Security Countermeasures
What specific office security measures are used by companies? There are four main office security measures.
Zoning
"Zoning” in office security measures refers to the division of offices according to the importance of security (security level). Zoning has the advantage of not only preventing information leaks from visitors, but also preventing unauthorized employees from accessing confidential information in a natural manner. In addition, zoning can be expected to improve work efficiency by taking into consideration the movement of people (lines of flow). In general, zoning is divided into four security levels as follows.
Security Level 1: Entrances, elevators, and other areas used by visitors.
Security Level 2: Areas shared by employees and visitors, such as lobbies and conference rooms.
Security Level 3: Areas used only by employees, such as work spaces and offices.
Security Level 4: Vaults, server rooms, and other areas where confidential information is managed.
Once the office is divided into these categories, security measures should be taken according to the level. For example, security cameras should be installed in all zones to provide evidence in case of trouble, and PIN numbers, ID cards, and biometric authentication systems should be used in zones above Level 3.
| The Bio-IDiom KAOATO face recognition packaged software can link face recognition to individual authorization andIt is ideal for restricting access to rooms according to security levels, as it can also be used as a deterrent by installing cameras.Please click here for a detailed explanation of Bio-IDiom KAOATO, including an overview, what it can do, and areas of application for facial recognition. About Bio-IDiom KAOATO |
|---|
Bio-IDiom KAOATO, a face recognition packaged software that is equipped with world's No. 1* rated face recognition engine and achieves high recognition accuracy, can be used for access control in offices and factories. Access control by face recognition can prevent unauthorized access to offices and factories while enhancing convenience.
- *
 No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
No. 1 in face recognition benchmark testing by the U.S. National Institute of Standards and Technology (NIST) multiple times to date. (Japanese text only)
NIST evaluation results do not constitute an endorsement by the U.S. government of any particular system, product, service, or company.
If your office is too small to use partitions, or if your visitors cannot see your computer screen due to the office layout, we recommend using movable partitions. Partitions can prevent visitors from peeking at internal data or knowing where important data is stored. However, when using partitions and partitions, be sure to check that you are not violating any laws or regulations, such as the Fire Service Act.
Utilization of Safe
The most important information in the company should be stored in a security level 4 location utilizing a safe. The safe to be used should be fireproof and burglar-proof, and employ a high-security locking method to prevent information leakage. The main locking methods include ten-key, dial, and finger vein authentication. Finger vein authentication is recommended because it is almost impossible to impersonate or forge. Finger vein authentication also has the advantage of being easy to unlock, since there is no need to remember a PIN number or how to turn a dial.
Set Security Camera
Security cameras can be installed in a variety of locations. For example, at entrances and reception areas where there is a lot of pedestrian traffic, or in elevators in enclosed spaces or in places where important information is managed, it is difficult to ascertain exactly what has happened in the event of trouble. However, if security cameras are installed in these locations, it is possible to determine how the trouble occurred and respond quickly. There is also the benefit of helping to deter crime simply by having cameras installed.Furthermore, installing cameras is not only a security measure, but also a deterrent to problems such as internal misconduct, sexual harassment, and power harassment, as it allows employees to check on their work, thereby improving operational efficiency.
Entry/Exit Control
A thorough access control system will prevent unauthorized entry by suspicious persons, thereby avoiding all risks, including human, physical, and information risks. A good access control system will also prevent unauthorized entry by unauthorized persons who enter together with authorized persons, thereby reducing the risk of information leaks and other problems.Some access control systems allow you to know who entered and left a room and when, so you can take action in the event of a problem such as an information leak. There are four main authentication methods: PIN authentication, IC card authentication, smartphone application authentication, and biometric authentication. These authentication systems are generally installed at gates and doors.
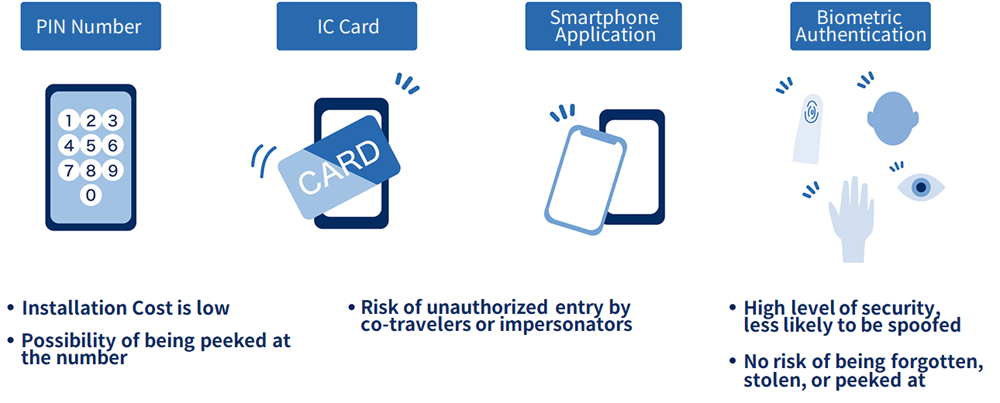
PIN is a method of unlocking a door by entering the correct PIN into a device installed in the door. It is inexpensive to install, and there is no risk of loss or theft, as is the case with IC cards. However, it is impossible to keep track of individual entry records, and if the PIN is peeked into, even outsiders can easily gain entry.IC card or smartphone application authentication is a method in which an IC card or smartphone is held over a reader device to unlock the door. Although it allows access control, there is a risk of unauthorized intrusion by co-conspirators or impersonators who target the timing of entry.Biometric authentication is a system that uses a part of the body for authentication, and includes fingerprint, face, vein, and iris authentication. Because each type of authentication uses biometric data unique to the individual, it is characterized by a high level of security and is less likely to be used for fraudulent purposes such as impersonation. There is no risk of “forgetting,” “theft,” or “prying eyes” as with other types of authentication.
5. Recommending Face Recognition System for Office Security Countermeasures
Unlike other biometric authentication systems, which offer a high level of security, face recognition systems are recommended for office security because of their convenience: users can be authenticated simply by pointing their face toward the camera, even if both hands are occupied. NEC Solution Innovator's face recognition system, in particular, allows users to enter the office stress-free, since there is no need to stop in front of the camera and the system performs “walk-through” face recognition while the user walks. The face recognition system is also highly secure, and while IC card authentication may be susceptible to fraudulent use, such as card borrowing and lending, identity theft, and taking someone with you, the face recognition system uses a camera to identify the individual, giving you peace of mind.
In addition, the risk of forgetting, losing, having the card stolen, or having it counterfeited cannot be eliminated with IC card authentication, and if such an event should occur, the IC card must be reissued, which is time-consuming and costly. However, with face recognition systems, there is no such risk, and there is no need to deal with the hassle and cost of dealing with such an eventuality.Furthermore, while other biometric authentication systems require a dedicated device, the face recognition system is easy to use, requiring only a web camera and a server for data storage (also available in the cloud).
Furthermore, NEC Solution Innovator's face recognition package software “Bio-IDiom KAOATO” automatically performs face registration after operation in response to changes over time once registered. This reduces the burden on employees (users) and eliminates the need for additional periodic registration for administrators. The system can also be linked to business systems and can manage employee overtime, making it a highly convenient system for managers.
We introduce the challenges of introducing access control systems, the effects of introducing face recognition systems, the types of authentication methods and the positioning of face recognition, and the reasons why Bio-IDiom KAOATO is chosen.
6. Summary
Thorough office security measures are very important for companies to protect all their assets and prevent loss of trust from customers and business partners. Zoning, installation of security cameras, and access control systems are effective office security measures, among which facial recognition systems are recommended due to their high level of security. If you are looking for a quick and easy-to-use security system, consider NEC Solution Innovator's facial recognition system, which offers many advantages to both managers and employees (users).
